« RSS Applications | Main | Software Tools »
Friday, November 06, 2009
Firefox Update
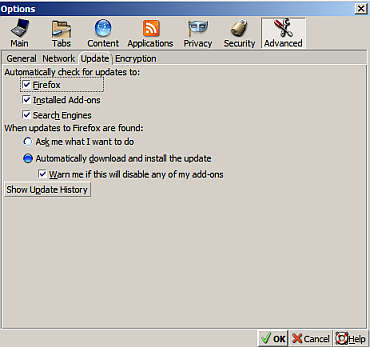
Y'all better check yer Firefox to see that you are running version 3.5.5 - if you aren't then run a manual upgrade (Help - Check for Upgrades). You might also set Firefox to automagically download and install upgrades:
| Categories: Best Practices, Mozilla Firefox, Security Alerts
Shockwave Player Update
Your Adobe Shockwave Player should be upgraded to version to 11.5.2.602 which is available here. Don't know if you actually have this POS installed? Go here - if you see an empty box at the top that says "Click here to download plugin," then you don't have Shockwave installed. If you use Firefox you should see a yellow box at the top of the page saying, "Additional plugins are required to display all the media on this page". The security inplications of NOT upgrading can be mitigated by using the Firefox Add-on Adblock Plus.
Sunday, November 01, 2009
Michael Duarf
Read this fine description of what bad guys are doing with your not-quite locked down Facebook account. If this sillyness keeps up I predict a large exodus from Facebook (starting with me). The fear of security breaches may be overblown but it is real. Don't be a victim. Remember, security is a process, not a product.Sunday, October 18, 2009
Facebook Hacking
A new applications on Facebook, "City Fire Department," has been compromised by hackers. The application had been modified to deliver an iframe which can bring content from one Web site to another. This iframe tries to exploit vulnerabilities to download a fake antivirus program called Antivirus Pro 2010.
A few of the other hacked or bogus applications are:
- MyGirlySpace
- Ferrarifone
- Mashpro
- Mynameis
- Pass-it-on
- Fillinthe
- Aquariumlif
Ok, here is the deal - When you find a wonderful new application on Facebook do a quick search on Google or bing to determine if anyone has had any problem with it. You can also wait, yes wait, for a day or two until enough newbies have started using it to provoke any disasters - if all is well after this then you might . . . might try it. Just make sure your Facebook preferences are locked down for maximum security. Or just don't use any of these silly applications until Facebook gets a grip and uses some mechanism to confirm these applications aren't a giant security hole!
| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Firefox Plugs Microsoft Security Hole
If you use Firefox (and you should, imho) you have probably already seen a pop-up alert informing you that it is blocking Microsoft`s .NET Framework Assistant and Windows Presentation Foundation add-ons that were stealthily installed by Microsoft earlier this year.
This hole was supposed to have been fixed earlier by having users edit the Windows registry - but this idea stunk because editing the registry is potentially dangerous. Microsoft later released a simple point and click removal tool - except this left behind the Windows Presentation Foundation plug-in which is what was just killed by Mozilla.
So, the confusion up to now has been addressed by both Mozilla and Microsoft to remove both nasty bits. Whew!
| Categories: Best Practices, Firefox Extensions, Mozilla Firefox, Security Alerts
Friday, October 09, 2009
Adobe Reader Critical Vulnerability
It appears the ever popular Adobe Reader (version 9.1.3 and earlier) has a gaping hole that could allow bad people to take over Windows installs. This problem as popped up before. One way to mitigate (but not eliminate) the threat is to disable Javascript in Adobe reader and/or change your browsers behavior to download .pdf files as opposed to view them. You also might want to try the free alternative called Foxit Reader which has a better record when it comes to security issues. Just sayin' . . .
| Categories: Alternative Applications, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Tuesday, August 25, 2009
Third-party apps create insecure Facebook
Popular social networking site Facebook has exposed users to phishing attacks that use already hacked accounts to contact friends. Links presented to users lead to look-alike pages not associated with Facebook that may hold any one of 11 rogue scripts (and counting) that do bad things. Trendmicro has details here.
Until facebook tightens up the ship now heading for the shoals be very careful about using third-party apps. Yes, that means a large chunk of facebook, sorry. Do this . . . no, seriously . . . and facebook will adapt or die. Now if Leafs fans would just do the same.
| Categories: Online Apps, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Wednesday, July 15, 2009
Critical Firefox 3.5 Security Flaw
The newest Firefox, version 3.5, includes Tracemonkey, a new feature designed to speed up Javascript scripts. A flaw within Tracemonkey could allow attackers to remotely install evil software when users visit compromised Web sites.
A simple fix is available until the next patch fixes the vulnerability:
- Open up a new Firefox window and type ‘’about:config‘’ (without the quotes) in your browser's address bar
- In the ‘’filter‘’ box, type ‘’jit‘’ and a setting called ‘’javascript.options.jit.content‘’ will appear.
- If the setting is set to ‘‘true’’ it means the option is enabled.
- If it is, double-click on the setting. This should change the option to ‘’false‘’ disabling it.
| Categories: Mozilla Firefox, Security Alerts, Virus-Trojan-Worm Alerts
Another Insecure ActiveX? You Betcha!
ActiveX flaws pop up on a regular basis so forget the explanation. Go to Microsoft and click the ‘’Fix It‘’ icon under ‘’Enable Workaround‘’ and following the instructions.
| Categories: Security Alerts, Virus-Trojan-Worm Alerts
Thursday, June 25, 2009
Security Update available for Shockwave Player
The bulletin and patch is here: http://www.adobe.com/support/security/bulletins/apsb09-08.html
Thanks, Security Fix
Tuesday, April 14, 2009
Twitter Awareness
The recent cross-scripting attack on the newest buzzword universe called Twitter is merely another bump on the rocky road through Interpipe 2.0
These XSS attacks are the bane of Web 2.0 and will cause disasters for individuals who refuse to become aware of their online surroundings. Compound this with users who remain clueless about what is running on their PC's and you have a large impediment in the push through to Web 3.0 applications.
Now add smartphones and netbooks to the mix ;(
For a fine write up on the Twitter XSS attack see: http://twittercism.com/protect-yourself-on-twitter/
Be sure to check out the fine tip from Twittercism about XSS busting using Firefox browser with the Add-on NoScript with screencaps from Better Safe Than Sorry here.
Edited on: Tuesday, April 14, 2009 12:07.58 PM EDT
| Categories: Adware/Spyware Alerts, Best Practices, Firefox Extensions, Mobile, Mozilla Firefox, Online Apps, Security Alerts, Virus-Trojan-Worm Alerts
Wednesday, March 11, 2009
.pdf Fixes Released
Adobe has released a newer fixed version of its Reader application that addresses previously documented problems. Those wishing to upgrade a previous release will have to wait until March 18th.
Those using the popular alternative, Foxit Reader, should upgrade their installed version by using the upgrade link under the help menu:
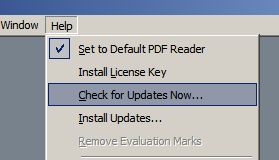
FoxitReader doing its thing:
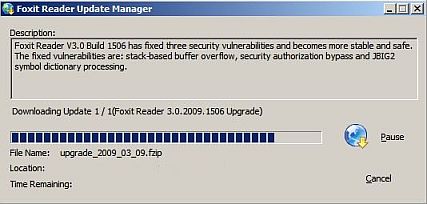
Success!
| Categories: Alternative Applications, Security Alerts
Friday, February 20, 2009
Adobe Reader Vulnerability
Evil-doers are actively exploiting a security hole in Adobe Reader. Users need only open a rogue .pdf file to have their system taken over.
Since Adobe doesn't plan to patch the problem until March 11th, 2009 users should either disable Javascript within Adobe Reader (Choose "Edit", "Preferences", "Javascript", and uncheck the box beside "Enable Acrobat Javascript") or use an alternative to Adobe Reader called Foxit Reader which is available here: http://www.foxitsoftware.com
| Categories: Alternative Applications, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Monday, January 19, 2009
Downadup Worm Awareness
The nasty worm dubbed Downadup.AL is reaching out and touching many people. F-Secure has a (beta) application to check your Windows system for infection - it's here: ftp://ftp.f-secure.com/anti-virus/tools/beta/f-downadup.zip. If you use Firefox browser (and why wouldn't you?) using the Add-on No-Script is a wise move to prevent this and other nasties from gaining a foothold into your system. Of course, running a software firewall, hardware router and and Anti-virus application is your best bet to remaining free of doom.| Categories: Adware/Spyware Alerts, Security Alerts, Virus-Trojan-Worm Alerts
Tuesday, January 06, 2009
Phishing Targets Tweeter
The popular mobile service Tweeter has been hit with phishing messages. Nothing new about this. It is a good time to remind folks about the devious nature of these evil doers. Any method will be used to induce the unwary or stupid to visit sites that will attempt to upload all kinds of malware, spyware, trojans, etc. to your PC, smartphone or other device. The vector for this specific attack is the very popular 'TinyURL' online application that turns large, unwieldy URLs such as “http://www.somewhere.orf/really/long/directory/” into something such as “http://tinyurl.com/4d4a2” which can be remembered long enough to key into a browser. The problem is that the TinyURL could lead one to evil sites. Very bad. TinyURL's solution, which folks either don't know about or don't use or understand is to use the Preview TinyURL. In our previous example one should append the TinyURL with preview: “http://preview.tinyurl.com/4d4a2”. This will allow for the best practice of safely viewing a rendering of the intended target before actually visiting it.| Categories: Best Practices, Headlines, Instant Messaging, Mobile, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Wednesday, December 17, 2008
IE Patched in Record Time
Microsoft has patched the critical flaw in its Internet Explorer browser in mere days. Good job! If you have Windows Automatic Update turned on you should already be patched depending on when you have set your PC to download and install the fix.
With more and more people aware of the problem it was incumbent upon Bill to fix the problem before even more folks ditched IE for more secure browsers such as Opera or Firefox. Either you're part of the problem or part of the solution and although Microsoft was late in embracing the Internet it seems they are moving towards being less of a vector for malware, spyware, viruses, etc. Let's hope the upcoming IE 8 is an even better experience for the vast number of users who, for some reason, never get the itch to try other browsers.
| Categories: Internet Explorer, Security Alerts
Sunday, December 14, 2008
Severe IE Vulnerability
An unpatched vulnerability in Internet Explorer 7 (which also affects older versions of the browser as well) is on the loose. Microsoft has stated that IE 5.01 with SP 4, IE 6 with or without SP 1 and IE 8 (Beta 2) on all versions of the Window OS are affected. To complete the horror IE 7 on Windows XP SP 2 and 3 and Windows Vista with or without SP 1 are also vulnerable. Web sites are now actively exploiting the vulnerability. One has to merely view a Web site in order to have a Trojan horse program automatically downloaded to their machine. Once downloaded the evil doers can manipulate the rogue program to download other software which could perform actions such as sending spam emails or steal data. Since Microsoft's next patch is not due until January 13, 2009 one would be wise to use an alternative browser such as Firefox or Opera. Just sayin' . . .| Categories: Mozilla Firefox, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Monday, November 10, 2008
WPA Cracked
If you use WiFi to connect to your Internet provider via a wireless router be aware that recently a crack has been found that could allow eavedroppers to detect your passphrase. The simple solution (for now) is to use WPA2 rather than the now vulnerable WPA. If by some chance you missed the memo about the much older WEP protocol you should have stopped using that years ago! If your router does not use WPA2 then ensure it is using AES encryption and not TKIP. Also be damned sure your passphrase is long (12+ characters minimum) and contains a mixture of lower case, upper case, numerals and characters. So, password IS NOT up to scratch. k*uh7%vg4Sk9jNVfdxq)( is just about right ;-)
| Categories: Best Practices, Headlines, Security Alerts
Wednesday, November 05, 2008
Critical Patches Released for Adobe Applications
Adobe has released patches that fix at least eight security holes in both its Acrobat and Adobe Reader programs. These flaws could be used by evil doers to take control of vulnerable systems. Versions 8.1.2 and earlier are affected. Adobe has rated these updates as “critical” indicating that the flaws could allow attackers to comptomise an unpatched system without the users knowledge. The Windows update may be found here.
| Categories: Best Practices, Security Alerts
Friday, October 24, 2008
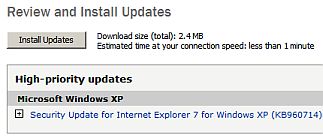
Critical Microsoft patch available
Microsoft has issued an out-of-band update. This is unusual as Microsoft rarely releases patches ahead of the usual once monthly Patch Tuesday. In this case the severity of the security hole has prompted them to wisely hurry the process along. This update is for XP and Vista although for Vista users it is not deemed critical. What the heck, do it anyway. If you have Windows Update all organized (as you should) you should be safe. If you are unsure if you already have the patch installed then go to Add/Remove Programs in the Control Panel, make sure the check box for show updates is checked:
and, when the list is finally displayed look for:
.jpg)
If it's not installed go back to the Control Panel and click on Security Center. Make sure all the settings for Windows Updates, your firewall and whatever anti-virus you use are all functioning as they should.
| Categories: Best Practices, Headlines, Security Alerts, Virus-Trojan-Worm Alerts
Tuesday, September 23, 2008
Facebook .zip attachment is Bad
People have been getting these fake Facebook 'Add Friends' emails.The evil-doers attached .zip file contains, wait for it you plugs, a Trojan Horse. C'mon, steady, don't fall for that old trick.
Unless you are expecting an attachment don't accept it. Anti-virus blah blah updated frequently blah blah backup daily blah blah idiot, don't be an ;)
| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Saturday, August 09, 2008
Facebook - MySpace Trojans
Both popular social networking sites, MySpace and FaceBook have both been attacked by an emailed virus that, should you download the plug-in as it suggests, sends large quantities of bogus emails. They contain trojans that Symantec has identified as gampass. This trojan is loooking for data on your system regarding gaming. Since this data may well include credit card numbers this is a problem. So, always be suspicious of any requirement for plugins above and beyond what you normally have installed. Keep your anti-virus software loaded and updated. Just because they are your friend on any social networking site does not mean they won't do something foolish that might well ensnare you. Remember, security is an ongoing process not a product.| Categories: Security Alerts, Virus-Trojan-Worm Alerts
Saturday, August 02, 2008
DNS Poisoning
DNS servers the world over have been targeted by evil doers. Flaws in these servers could allow creeps to silently redirect your browser sessions to anywhere.
To check to see if your ISP is vulnerable go here.
If the results (above) are less then satisfactory do contact your ISP and complain bitterly.
You could also use DNS servers that are patched. I suggest OpenDNS.com - they even have a handy application that corrects your settings when your ISP's DHCP server changes your IP.
Here is a good synoposis from the blog Security Fix:
At issue is a basic design flaw in the domain name system. DNS is the communications standard that acts as a kind of telephone book for the Internet, translating human-friendly Web site names like example.com into numeric addresses that are easier for networking equipment to handle and route. When people type a Web site name into their Internet browser, the process of routing of that name to Internet address is generally handled through DNS servers managed by Internet service providers and corporations. But according to research released this month, most of those DNS servers are vulnerable to a security flaw that allows miscreants to silently alter the virtual road maps that those systems rely on to route traffic. As a result, a cyber criminal could trivially rewrite those records so that when customers of a vulnerable ISP or network provider try to visit a particular Web site, they are instead taken to a counterfeit site created by the bad guys.
Security begins at home. Never assume your ISP has a clue.
| Categories: All Things Mac, Headlines, Security Alerts
Thursday, July 31, 2008
Realplayer Patch Released
RealNetworks has released a patch to correct a flaw in its RealPlayer software that could allow evil code to be run on client computers. Run the updater to download and install that fix.Edited on: Thursday, July 31, 2008 7:14.56 PM EDT
| Categories: Security Alerts
Wednesday, June 04, 2008
Evil Hewlett-Packard support application
If you use an HP computer chances are it has a pre-installed customer support application that has been found to contain multiple security vulnerabilities. The software is designed to make it simple for users to automatically update HP drivers and software. However, flaws in ActiveX components within the HP Instant Support allow drive-by download attacks in cases where users unwittingly visit insecure websites.
HP Instant Support HPISDataManager.dll version 1.0.0.22 and earlier are affected. Users should upgrade to version 1.0.0.24.
To install the upgrade HP users should visit "http://www.hp.com/go/ispe" and choose “launch an online diagnostic session".
| Categories: Adware/Spyware Alerts, Security Alerts, Virus-Trojan-Worm Alerts
Their problem could be your problem
It appears the website of an Ottawa recreation centre may have been the victim of a SQL injection attack that infected guests computers with a computer virus leaving them vulnerable to various nasties including spam, fraud or identity theft. The Ray Friel Recreation Centre was infected between May 14 - 21, 2008.
Those with up to date Anti-virus and spyware protection using Firefox or Opera browsers had little to fear but others may not have been so lucky. Mac users are safe ;-)
Remember, be alert because the world needs more lerts . . .
| Categories: Security Alerts, Virus-Trojan-Worm Alerts
Wednesday, May 28, 2008
Patch your Flash NOW
| Categories: Alternative Applications, Mozilla Firefox, Privacy Issues, Security Alerts, Software Tools, Virus-Trojan-Worm Alerts
Tuesday, January 22, 2008
How to kill ActiveX
ActiveX is generally a gross security problem waiting to happen within Internet Explorer. Having the ability to kill certain (A few? Some? All but what you really need?) ActiveX controls is detailed by Microsoft here. Or you could use Opera or Firefox in place of Internet Explorer.| Categories: Alternative Applications, Privacy Issues, Security Alerts
Tuesday, November 27, 2007
Unpatched QuickTime Flaw
Those using QuickTime should be aware that a flaw in the most current version could allow attackers to execute code remotely on users machines. While there is no patch available CERT has posted various workarounds to minimize the risk.| Categories: Adware/Spyware Alerts, Privacy Issues, Security Alerts
Saturday, October 20, 2007
RealPlayer Exploit
User of Internet Explorer under Windows are vulnerable to drive-by downloads simply by visiting an evil Web page. As usual, it is an unknown and unpatched ActiveX component that is causing the problem. Note that both Microsoft Outlook and Outlook Express clients are also at risk. Best practices? Uninstall RealPlayer, use an alternative browser such as Firefox or Opera and use another email client such as Thunderbird or Penelope. Those who just can't part with RealPlayer should visit http://service.real.com/realplayer/security/en/ and (when available) download and install the patch. Ryan Naraine over at ZDNet.com has a great write up with info and fixes.| Categories: Adware/Spyware Alerts, Alternative Applications, Best Practices, Mozilla Firefox, Mozilla Thunderbird, Opera, Penelope Email, Privacy Issues, Security Alerts
Thursday, July 19, 2007
OS X Something!
No, I have not RTFA. I do know that having faith that a certain OS is more secure than others is, one day, going to cause . . . problems.| Categories: All Things Mac, Security Alerts, Virus-Trojan-Worm Alerts
Wednesday, July 04, 2007
Mpack Intrusion Means Patch Often
Brian Krebs over at the Blog Security Fix has mentioned the availability of the Mpack hackers kit which allows anyone with cash to make serious intrusions into computers and networks. This kit works because folks don't patch all the software on their Windows machines in a timely fashion. If your Windows Operating System is secure but all the software you run is old and unpatched you are vulnerable to this threat. Best Practice? Click on the 'Secunia Software Inspector' icon over in the left column and let Secunia inform you what needs patching. Also sign up for email updates so Secunia can inform you when to re-run the test.| Categories: Best Practices, Security Alerts
Sunday, June 17, 2007
Safari Browser for Windows (Beta)!
This appears to be the platform by which Apple might require you to have if you wish to use the next version of the iPhone. Except the browser compares poorly to others as it appears to not load faster. It has security issues ( don't they all ) andEdited on: Wednesday, July 04, 2007 2:08.22 PM EDT
| Categories: Headlines, Mac Safari Browser, Security Alerts
Monday, June 11, 2007
OpenOffice.org Virus Spreads
A virus written in numerous scripting languages that can affect Windows, Linux, and Mac OS X computers is slowly spreading via infected OpenOffice.org documents. Best practice is, of course, to never accept documents as attachments in email if you were not expecting them. Inform the sender that it is always best to announce attachments before sending. Having a good Anti-Virus and firewall is also an excellent idea just in case nasties end up on your system. Better safe than sorry!| Categories: Adware/Spyware Alerts, Alternative Applications, Best Practices, Openoffice.org, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Friday, June 08, 2007
Yahoo Messenger Critical Upgrade
Yahoo Messenger has released an upgrade to fix a known security hole that would allow attackers to execute code on your PC. Please upgrade to version 8.1.0.401 from here: http://messenger.yahoo.com/download.php| Categories: Adware/Spyware Alerts, Alternative Applications, Best Practices, Instant Messaging, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Wednesday, May 23, 2007
Abandon hope all ye who enter!
Aargh! Is this safe? I am not believing this!
Edited on: Wednesday, May 23, 2007 4:23.27 PM EDT
| Categories: Security Alerts
Monday, May 14, 2007
Google: 1 in 10 Websites Unsafe
Especially if you use Internet Explorer as opposed to Firefox or Opera. The chance of being nailed by a "drive-by download" is almost non-existent when using any browser other than Internet Explorer. Do yourself a favour and try a safer alternative.
| Categories: Adware/Spyware Alerts, Alternative Applications, Headlines, Mozilla Firefox, Opera, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Sunday, April 01, 2007
Flaw Allows Critical Windows Exploit
"Upon viewing a Web page, previewing or reading a specially crafted message, or opening a specially crafted e-mail attachment, the attacker could cause the affected system to execute code," sez Microsoft in its advisory. Using any version of Windows, including Vista, and Internet Explorer could lead to catastrophe merely by viewing a web site. Simply viewing an .html page as displayed by most email clients such as Outlook Express could lead the same result. Best Practices? Consider using another browser such as Opera or Mozilla Firefox and/or another email client such as Thunderbird.| Categories: Alternative Applications, Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, March 15, 2007
Phishing vulnerability in IE7
Secunia has a test page where you can determine if your browser is effected. Our tests show Mozilla Firefox 2.0.0.2 and Opera 9.10 to be safe. Internet Explorer 7.0.5730.11 is unsafe. Best practise: Do not use Internet Explorer except to obtain updates for your Windows OS.| Categories: Privacy Issues, Security Alerts
Monday, March 05, 2007
QuickTime Flaw Patched
Apple has patched its QuickTime application for both Mac OS X and all flavours of Windows from 2000 to Vista. Update your version NOW via the software update feature or by going to: http://www.apple.com| Categories: Privacy Issues, Security Alerts
Sunday, January 07, 2007
Time to upgrade Opera to 9.10
A recent security hole in any version of Opera prior to version 9.10 should spur you slowpokes into upgrading. If you haven't tried Opera browser you should. Opera is the most secure browser of the big three (Internet Explorer & Mozilla Firefox being the other two) running under Windows. Other features include Opera Voice (voice commands for the browser), & Widgets (mini displays of info you choose) and BitTorrent (ask your teenagers...!). Try it - love it or hate it, there is always Firefox ;-)| Categories: Alternative Applications, Opera, Security Alerts
Saturday, January 06, 2007
Adobe Acrobat .pdf Exploit
A serious vulnerabilty in Adobe Acrobat Reader versions prior to version 8 leaves Windows machines open to various attacks. Users, and lets face facts here, that means everyone, should upgrade to version 8.If an upgrade is impossible or unfeasable then, until a patch is issued you should, according to Adobe, disable the Adobe Acrobat Reader plug-in for your Internet browser.
Adobe has the details here: http://www.adobe.com/support/security/advisories/apsa07-01.html
| Categories: Privacy Issues, Security Alerts
Tuesday, January 02, 2007
Apple Quicktime Exploit
A highly critical security hole affecting Apple QuickTime version 7.1.3 (or earlier versions) has been exposed. Users of Quicktime are advised to disable Real Time Streaming Protocol. Windows XP users navigate to: Edit –> Preferences -> Quicktime Preferences -> File Types tab : uncheck ‘’Streaming - Streaming Movies‘’. Secunia has suggested users be very wary of opening files with the extension .qtl hosted on sites that look in any way dodgy.| Categories: All Things Mac, Security Alerts, Virus-Trojan-Worm Alerts
Monday, January 01, 2007
Time to update your now expired Windows Defender
If you have been using Windows Defender it is time to update as the previous version has now expired. It may be downloaded here.Sunday, December 31, 2006
Be Careful of Holiday Greetings Attachments
Since this is the season to sent and receive pictures, songs, and other greetings you must be extra alert to the hidden dangers of email attachments containing evil crap. As always, the best practice is don't click on any link you have doubts about and delete any attachments you were not expecting. Should you in error activate one of these evil things your anti-virus software should stop it. You do have anti-virus software, right?| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Saturday, December 16, 2006
Yahoo IM client flaw is patched
If you use Yahoo! Messenger IM client you should immediately upgrade to fix a highly critical breach that opened up. Visit Secunia at: http://secunia.com/advisories/23401/. Yahoo! has the information here.| Categories: Alternative Applications, Instant Messaging, Security Alerts
Saturday, December 02, 2006
Quicktime movies phishing MySpace.com users through Internet Explorer
Quicktime .mov files have been exploited in order to, at least in part, launch phishing attacks against myspace.com patrons. The SpywareGuide Greynets Blog summerized it thus: 1) A new Myspace worm 2) Bad guys using HREF functionality available to Quicktime files 3) Hacked websites hosting fake Myspace login details 4) A pornographic website (linked to from various hacked profiles) that contains Zango content, as well as using a popunder to display more Zango videos. More info is here and here.| Categories: Security Alerts, Virus-Trojan-Worm Alerts
Friday, November 24, 2006
Firefox Password Manager Compromised
It seems a flaw in the way Firefox handles passwords is enabling evil doers to create Phishing holes at sites where .html is allowed such as myspace.com - no fix has been issued but Secunia is advising users to disable the "Remember passwords for sites" option in Firefox preferences.| Categories: Best Practices, Mozilla Firefox, Security Alerts
Tuesday, October 31, 2006
ZoneAlarm Auto-Update Alarms Users
If you use the ever popular software firewall ZoneAlarm you will have recently seen the first appearance of the new Auto-Update dialogue box indicating that ZA has successfully patched itself. One discussion appears here. Screencaps of the glorious moment are here. If you haven`t spotted the dialogue box it is likely you neglected to download and install the last "full" version which must have included the Auto-Update feature. You are bad, very bad. Update your old ZoneAlarm and bask in the glory of a new Auto-Update tomorrow. (cue triumphant music) Now, why did they not inform its user base of this welcome development before the fact? This is the kind of action that generally prompts me to do a full uninstall as I worry about other processes launching behind my back. Arrgh. I look forward to the full explanation of this behaviour as should you.Edited on: Friday, December 01, 2006 1:13.29 AM EST
| Categories: Best Practices, Headlines, Privacy Issues, Security Alerts
Wednesday, October 18, 2006
Hardware Mayhem
First, it was promotional mp3 players from McDonald's Japan that contained a trojan now it's some Apple Video IPods that shipped with a virus. So, the mantra you must repeat is, "Security is a process NOT a product." Best Practices? Be aware of the possibility of viruses, trojans, etc. appearing in all manner of places and have your defences (Anti-Virus, Firewall, Spyware killers, etc.) ready before you are infected.| Categories: All Things Mac, Best Practices, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Monday, October 02, 2006
USB as CD-ROM
Be aware of the| Categories: Hardware Innovations, Privacy Issues, Security Alerts
Tuesday, September 26, 2006
Windows Vector Markup Language (.VML) Patch
Microsoft has released a patch that fixes the vulnerability found in .VML files. Since this patch has been released outside of the normal update schedule some folks may miss this patch. If this is you then run Microsoft Update NOW.| Categories: Best Practices, Security Alerts
Thursday, September 21, 2006
Windows Vector Markup Language (.VML) Exploit Criticial
Time to unregister a (.dll) file from your Windows XP. If you don't and you use Internet Explorer as your browser you are taking a risk of being owned. This exploit is a drive-by download and you won't even know you're beat. So, Start . . . Run . . . and enter all this:regsvr32 /u "%CommonProgramFiles%\Microsoft Shared\VGX\vgx.dll". . . and hit Return . . . whew, that was close, hmm?| Categories: Best Practices, Security Alerts
Wednesday, August 09, 2006
Patch Tuesday From Microsoft
If you have neglected to run Windows Update today you really must and be damn quick about it. Major security issues leave you vulnerable unless you update. Now.Tuesday, August 01, 2006
McAfee Flaw
McAfee's whole slew of consumer products is at risk from a flaw that can expose information stored on Windows PC's. Information is here and here. Perhaps it's time to consider an alternative applications such as AVG Free for virus protection?| Categories: Alternative Applications, Headlines, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Friday, July 21, 2006
MS PowerPoint Attachment Trouble
If you receive an email from an unknown Gmail address and it contains an MS PowerPoint presentation then delete it.Edited on: Monday, July 31, 2006 4:27.20 PM EDT
| Categories: Adware/Spyware Alerts, Alternative Applications, Mozilla Firefox, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, July 13, 2006
Adobe Acrobat 'Highly Critical Flaw'
A highly critical flaw has been detected in Adobe Acrobat version 6.0.4 and earlier. If this is you, and it probably is, get thee hence to: http://www.adobe.com/support/downloads to obtain version 6.0.5 or launch Acrobat and use the Auto Update feature.Edited on: Monday, July 31, 2006 4:27.13 PM EDT
| Categories: Best Practices, Privacy Issues, Security Alerts
Saturday, July 08, 2006
Macromedia Flash Player Update
The most recent version is available here:http://www.adobe.com/products/flashplayer/. This fixes a few security boo-boos and is a must have download.Edited on: Monday, July 31, 2006 4:27.03 PM EDT
| Categories: Adware/Spyware Alerts, Privacy Issues, Security Alerts
Friday, June 30, 2006
OpenOffice 2.0.3 Released
This is a must have download that takes care of three recent security holes.Edited on: Monday, July 31, 2006 4:26.55 PM EDT
| Categories: Alternative Applications, Openoffice.org, Security Alerts
Thursday, June 15, 2006
MSN Messenger Worm Spreads
A new worm that seems to be based on an old design (BlackAngel.B / W32/BlackAngel.B.worm) is slowly spreading over the MSN. If you use MSN for chatting only accept files from people and/or sources you trust - even then take all the usual precautions. Best practise is to use a safer IM client such as GAIM for chatting and ONLY chatting - file transfers are best accomplished other ways if you must.| Categories: Alternative Applications, Best Practices, Instant Messaging, Security Alerts
Tuesday, June 13, 2006
Yahoo! Worm on the Loose
A mass emailer is currently spreading through Yahoo! The worm is activated by simply opening the email message thus making it quite dangerous. The subject line to watch for is: "[random word] New Graphic site".Yahoo is working on the problem. More info here.Edited on: Monday, July 31, 2006 4:26.26 PM EDT
| Categories: Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, June 08, 2006
AutoRun - Tool of the Devil
If you found a USB storage device at your workplace would you plug it into your PC?Edited on: Monday, July 31, 2006 4:26.15 PM EDT
| Categories: Best Practices, Privacy Issues, Security Alerts
Wednesday, May 24, 2006
IM Worm Targets Yahoo Users
A worm dubbed yhoo32.explr is spreading across Yahoo's IM network. It forwards itself using the contact lists of people whose computers have already been infected. If installed it hijacks the browser home page steering the users to an evil site that attempts to load spyware.| Categories: Adware/Spyware Alerts, Alternative Applications, Instant Messaging, Security Alerts, Virus-Trojan-Worm Alerts
Friday, May 19, 2006
W32/Ginwui.A Word Trojan
In these trying times why not try an alternative to Microsoft Word such as Openoffice.org?Edited on: Saturday, May 20, 2006 9:33.12 PM EDT
| Categories: Alternative Applications, Openoffice.org, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Wednesday, May 17, 2006
Poker Players Beware!
If you downloaded RBCalc.exe as distributed by checkraised[dot]com then you have a rootkit on your system! Always check downloads before you make them to ensure they are safe.| Categories: Adware/Spyware Alerts, Best Practices, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Monday, May 15, 2006
Mac Patches You Need
Apple has patched some 31 flaws but according to reports (here and here) there are still flaws that won't be addressed for some time to come :-(| Categories: All Things Mac, Mac Safari Browser, Privacy Issues, Security Alerts
Thursday, May 11, 2006
Firefox mailto: exploit
This exploit could cause your default email client to launch allowing spam to escape. Or it could simply slow down your PC. The quick 'n dirty fix is here.| Categories: Best Practices, Mozilla Firefox, Privacy Issues, Security Alerts
Friday, May 05, 2006
Yahoo Profile Phishing
If you use Yahoo! for IM or email then beware of this phishing web page that spoofs a typical Yahoo! profiles login page hosted on a domain named yahoo-members.com.| Categories: Privacy Issues, Security Alerts
Friday, April 14, 2006
Firefox Update Available
The latest version of Firefox that includes several important security updates is available. Click Help . . . Check for Updates.| Categories: Best Practices, Mozilla Firefox, Security Alerts
Sunday, April 09, 2006
Winamp 5.13 Released
Nullsoft has released a new version of Winamp, version 5.13, that fixes a recent vulnerability. If you are using Winamp as your media player you should download and install this update.| Categories: Security Alerts, Virus-Trojan-Worm Alerts
Thursday, March 30, 2006
Flexispy.A Symbian 60 Trojan / Keylogger
This nasty litle piece of work is actually a commercial product named Flexispy! It records information about voice calls and text messaging sessions. The information is sent to a company server where it can be viewed on the web. Now, I can imagine many scenarios where this type of application could be used in a positive manner but lets get realistic and assume it will be used for nefarious purposes. F-Secure has all the details.| Categories: Adware/Spyware Alerts, Mobile, Privacy Issues, Security Alerts, Software Tools, Virus-Trojan-Worm Alerts
Tuesday, March 28, 2006
Unofficial IE Patches Available
Since Microsoft has announced no patch would (likely) be available for the latest IE vulnerability until April 11, 2006 two patches, here and here, have been authored. Completely unofficially of course but if folks must use Internet Explorer then best practise is to install one of these patches. This is not the first time folks have “stepped into the breach” to cover Bill`s a**.| Categories: Best Practices, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Monday, March 27, 2006
Internet Explorer Vulnerability Escalates
Reports state that over 200 legitimate websites have been infected with the source code of the latest Internet Explorer exploit. This means that even “safe” sites could potentially harvest data from your PC. Again, for now either disable IE's active scripting option or use any other browser.| Categories: Security Alerts, Virus-Trojan-Worm Alerts
Friday, March 24, 2006
Internet Explorer Vulnerability
Microsoft is reporting an unpatched flaw in Internet Explorer that could allow evil site owners to take over local machines. For now either disable IE's active scripting option or use any other browser such as Firefox or Opera.| Categories: Security Alerts, Virus-Trojan-Worm Alerts
Tuesday, February 28, 2006
Java Trojan RedBrowser-A Targets Cell Phones
Evildoers have created a Trojan that targets cell phones running Java. Found by Kaspersky Lab this puppy infects any device capable of running Java applications. The text is only in Russian so far so the chance of running into this outside of that country is small. The threat is that someone may reverse engineer it for other countries so keep on your toes. This Trojan pretends to be a WAP browser offering free browsing via SMS messages. Since many companies the world over offer cheap or free SMS the victim is tricked into believing they are able to browse the Web for free. In reality the trojan sends SMS messages to one specific number that will charge back a premium amount on the victims cell phone bill. Best Practices circa 1878: If it sounds to good to be true it probably is. Best Practices circa 2006: If it sounds to good to be true Google it.| Categories: Bluetooth, Instant Messaging, Mobile, Security Alerts, Virus-Trojan-Worm Alerts
Tuesday, February 21, 2006
Mac Safari Browser Vulnerabilty
Secunia is reporting on a vulnerability in the Safari browser caused by an error in the processing of file association meta data (found in the "__MACOSX" folder) in .ZIP archives. This could cause users to execute a malicious shell script that has been renamed to a safe file extension stored in a .ZIP archive.Worse, it can also be exploited automatically when Safari visits an evil web site.
Secunia has a test available to confirm if your system is vulnerable: http://secunia.com/mac_os_x_command_execution_vulnerability_test/
The vulnerability can be lessened by disabling the "Open safe files after Downloading" option in Safari.
| Categories: All Things Mac, Mac Safari Browser, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Saturday, February 18, 2006
Later? NO . . . NOW!
According to InfoWorld evildoers have already released Malware that targets flaws in Microsoft products that were patched yesterday. So, those of who have your Windows Update on Automatic are safe but those of you who manually initiate the downloads or who casually thought, "Nah, I'll do it Sunday when I have time" may already be in a world of bad.It is a good idea to set your Windows Update to anything but 'Turn off Automatic Updates'. In fact, if you are the procrastinating type then you should not use 'Notify me but don't automatically download or install them' because by the time you get around to it it may be too late.
If you frequently start up and shut down your PC it may be that even 'Download updates for me, but let me choose when to install them' won't work for you but please try it.
Your best bet is to use 'Automatic (recommended)' so there is no delay in patching your box. If your routine is to boot up your PC every morning at 7:00 AM and start downloading your email whle you brew the coffee why not set your update time to coincide with it? No muss, no fuss. Don't you feel better all ready?
Start - Settings - Control Panel - Security Center: Click Automatic Updates ;-)

Automatic Updates Dialogue Box:
| Categories: Best Practices, Security Alerts
Friday, February 17, 2006
Mac OS X Bluetooth (Proof of Concept) Worm
When it rains it pours for you Macheads. F-secure received a sample virus, Inqtana.A, that spreads via the Bluetooth OBEX Push vulnerability described here: http://www.osvdb.org/displayvuln.php?osvdb_id=16074. The exploit is not in the wild and will expire on February 24, 2006 but to be safe from this threat now and in the future you are advised to install the latest patches for your OS X version 10.4 ASAP.| Categories: All Things Mac, Bluetooth, Headlines, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, February 16, 2006
First Mac OS X Virus
The first virus for Mac OS X has been encountered today. Called OSX/Leap.A. by F-Secure the Malware was posted via a link to MacRumors forum. Supposedly a screenshot for Mac OS X v10.5 Leopard the virus spreads through iChat.It appears the victim must be running in Admin. mode to be infected. As with any OS you should generally not be swaning around while in Admin. mode because of the risk of compromising your PC at the "root level" where all the important processes live. If these processes are taken over by rogue software you can lose complete control without even knowing it.
Do yourself a favour and make a new user on your Windows box with less than Admin. privileges before you go wandering off into the Interweb.
| Categories: All Things Mac, Headlines, Instant Messaging, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, February 09, 2006
IE7 beta released + weird behaviour
The beta version of Microsofts Internet Explorer 7 is available for download. Please note that as a beta release this experimental software could cause untold havoc on your PC so unless you are OK with that wait until the first real version is released. I have done so and am impressed by the anti-phishing tool and with the inclusion of the ever popular 'Spoofstick'. Along with tabbed browsing and a sort-of decent RSS feed detector this browser will at least help to protect the hundreds of thousands of folks who are as yet clueless to the fact that IE6 is a security hole that you will eventually fall into!One strange bit of action I am unhappy with is the occasional behind the scenes execution of a scheduled task called "System_Feed_Sync_Scheduler.job" which is I assume the RSS feed checking for updates except I don't have IE7 running when it happens!
If you check your %Windir%tasks\ directory you will see two new jobs:
- System_Feed_Rescheduler
- System_Feed_Sync_Scheduler
Both jobs accesses "rundll32.exe" and "msfeeds.dll" which appears to be how Bill updates yer feeds.
I am no expert but it seems registering new scheduled events with privileges could be a problem?
| Categories: RSS Applications, Security Alerts
Monday, January 30, 2006
Winamp 5.x Exploit
Secunia reports on an exploit that may allow evildoers to compromise a user's system. The exploit is publically available so until a patch is issued use one of many other programs in place of Winamp.Saturday, January 21, 2006
Nyxem.e Email Worm Spreading Fast
This puppy is really spreading fast - over 500,000 PC's are likely infected and when the trojans payload is released on the 3rd of February it could get much worse. Users need to practise safe emailing to avoid this and other nasties. F-secure has the details here: http://www.f-secure.com/v-descs/nyxem_e.shtml.| Categories: Security Alerts, Virus-Trojan-Worm Alerts
Monday, January 16, 2006
Windows WiFi Vulnerability
The Washington Post reports a flaw related to ad-hoc networks on WiFi enabled Windows 2000 or XP machines. The solution, at least until Microsoft patches the flaw, is to use a firewall - this prevents the exploit. The blog has full details: http://blogs.washingtonpost.com/securityfix/2006/01/windows_feature.html.| Categories: Best Practices, Privacy Issues, Security Alerts
Thursday, January 12, 2006
Norton SystemWorks Patch
Symantec has patched its Norton SystemWorks following the discovery of a security vulnerability. Users are advised to run LiveUpdate ASAP.| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, January 05, 2006
WMF Exploit Official Microsoft Patch Available
Microsoft has released the official patch designed to close the WMF exploit. If you are running Microsoft Windows 2000 with Service Pack 4 download from here: http://www.microsoft.com/downloads/details.aspx?FamilyId=AA9E27BD-CB9A-4EF1-92A3-00FFE7B2AC74. If you are running Microsoft Windows XP with Service Pack 1 or 2 download from here: http://www.microsoft.com/downloads/details.aspx?FamilyId=0C1B4C96-57AE-499E-B89B-215B7BB4D8E9.| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Wednesday, January 04, 2006
WMF Exploits via Email, Part 2
The latest email using the WMF exploit purports to come from Yale University. If the link within the email is clicked then the exploit launches. This evil site also attempts to exploit flaws found in older versions of Firefox - another reason to upgrade to the latest Firefox. Unless you are protected as previously outlined (here, here, here and here) you are screwed! Welcome to the Internet! Sheesh. Please add the following entries to your ever expanding hosts file:
- playtimepiano[dot]home[dot]comcast[dot]net
- 86[dot]135[dot]149[dot]130 # UDP
- 140[dot]198[dot]35[dot]85:8080 # IRC
- 24[dot]116[dot]12[dot]59:8080 # IRC
- 140[dot]198[dot]165[dot]185:8080 # IRC
- 129[dot]93[dot]51[dot]80:8080 # IRC
- 70[dot]136[dot]88[dot]76:8080 # IRC
Please note that [dot] (above) should be replaced with .
| Categories: Security Alerts, Virus-Trojan-Worm Alerts
Sunday, January 01, 2006
WMF Exploit Unofficial Patch
Tests performed on various machines protected by up to date Anti-virus applications have shown that they are almost powerless to stop this series of WMF exploits. On top of the previous best practices an unofficial patch has been released. Understand that Microsoft has no hand in this so if it breaks your OS you are on your own. Since Microsoft appears to not have a fix in the works for a long while this patch is likely a good move until an official fix is released.Remember to first run the command "regsvr32 -u %windir%\system32\shimgvw.dll" (without the quotes) from START - RUN. Assuming you get the OK that the "Microsoft Picture and Fax Viewer" was successfully unregistered then run the patch found here: http://handlers.sans.org/tliston/wmffix_hexblog11.exe.
| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
WMF Exploits via Email
The emails Subject line is: "Happy New Year" and the Body says: "picture of 2006". Included is an attached exploit WMF file named "HappyNewYear.jpg". When the HappyNewYear.jpg is accessed (file opened, folder viewed, file indexed by Google Desktop) it executes and downloads a backdoor trojan from www[dot]ritztours.com. Please add this domain to your hosts file and make sure your Anti-virus is up to date.| Categories: Security Alerts, Virus-Trojan-Worm Alerts
Saturday, December 31, 2005
2005 List of (Known!) OS Vulnerabilities
Nothing says 'end of year' like a big honking list of all (known) vulnerabilities in various operating systems.Read it and be afraid, very afraid: http://www.us-cert.gov/cas/bulletins/SB2005.html.
Happy New Year!
| Categories: Headlines, Security Alerts
Thursday, December 29, 2005
Windows Metafiles (.WMF) Exploits Continue, Part 2
Microsoft has explained how to unregister the Windows Picture and Fax Viewer (Shimgvw.dll):
- Click Start, click Run, type "regsvr32 -u %windir%\system32\shimgvw.dll" (without the quotation marks), and then click OK.
- A dialog box appears to confirm that the un-registration process has succeeded. Click OK to close the dialog box.
NOTE: The Windows Picture and Fax Viewer will no longer open when yous click on a link to an image type that is associated with the Windows Picture and Fax Viewer.
To undo this change, re-register Shimgvw.dll by following the above steps:
- Click Start, click Run, type "regsvr32 %windir%\system32\shimgvw.dll" (without the quotation marks), and then click OK.
- A dialog box appears to confirm that the registration process has succeeded. Click OK to close the dialog box.
| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Wednesday, December 28, 2005
Windows Metafiles (.WMF) Exploits Continue
It appears the real time indexing of metafile data using Google Toolbar is enough to exploit the payload. For now you should disable this indexing of media files until Microsoft issues a patch.You should also add the following sites to your hosts file:
- Crackz.ws
- unionseek.com
- www.tfcco.com
- Iframeurl.biz
- beehappyy.biz
| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
There is no "MSN Messenger 8 Working BETA" !
So don't be clicking those links to download a copy even if the Instant Message comes from a friend. Especially if that friend is not as security aware as you. All you MSN Messenger users read this: http://www.infoworld.com/article/05/12/27/HNmicrosoftvirkelvirus_1.html and this: http://www.f-secure.com/weblog/archives/archive-122005.html#00000751.| Categories: Instant Messaging, Security Alerts, Virus-Trojan-Worm Alerts
Windows Metafiles (.WMF) Exploits
You might add unionseek[DOT]com to your host file. The site is using images, specifically .WMF files (Windows Metafiles), to carry a payload of trojans. Internet Explorer is vunerable, older versions of Firefox and Opera are also at risk but at least they prompt users before they launch external applications ("Windows Picture and Fax Viewer") to view the image. F-secure has the details here: http://www.f-secure.com/weblog/archives/archive-122005.html#00000752. The first I saw of it was at The Register: http://www.theregister.co.uk/2005/12/28/messenger_virus/.| Categories: Alternative Applications, Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, December 22, 2005
IM Trojan on the Loose
Various reports, including this one: http://news.zdnet.com/2100-1009_22-6002790.html, have a new Instant Messaging trojan being sent to AOL, MSN and Yahoo users. The link, to some lame Santa whats-it, also installs a Rootkit on users Windows PC. The links arrive from people on users "buddy lists" so folks are not as suspicious as they might otherwise be. Remember to never click, download, accept attachments, etc. unless you have been informed before the fact that they are on the way.| Categories: Instant Messaging, Security Alerts, Virus-Trojan-Worm Alerts
Monday, December 19, 2005
Bluetooth Vulnerability
The folks at digitalmunition.com have found a security hole in most Bluetooth software. The skinny is here: http://www.digitalmunition.com/DMA%5B2005-1214a%5D.txt. F-secure has an overview of the problem here: http://www.f-secure.com/weblog/archives/archive-122005.html#00000741.| Categories: Best Practices, Bluetooth, Privacy Issues, Security Alerts
Wednesday, December 14, 2005
Fake McAfee Site via Email Links
F-Secure has reported instances of fake emails from McAfee with links that point to a bogus site with downloads that contain viruses. Applications do not update themselves by having their parent company send emails encouraging users to visit sites. Be aware what software is installed on your PC. Determine which of these update automagically and keep a grip on what URL's correspond to what websites. If in doubt do not click that link! Never respond to unsolicited emails.| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
The Thirty Day Rule
An old Javascriprt vulnerability in all Firefox versions prior to 1.0.5 has taken on a new life since the code to take advantage of it has been published on the web. Those of you who are still happily using older versions should upgrade. Best Practices: Always upgrade to the latest version of software at about the thirty daymark after its release because . . . a) This gives any bugs in the release time to be found by all those early adopters allowing the developers time to patch the bug. b) Not enough time has passed that evil virus writers have released exploits. c) Authors of plugins and other add-ons (such as Firefox extensions) will have had time to patch their products.| Categories: Best Practices, Mozilla Firefox, Security Alerts
Thursday, December 08, 2005
Sony Rootkit Patch Needs Patch
The Sony Rootkit saga lurches ever onward with news that the recently issued patch can, according to Cnet, ". . . allow Sony's original patch to trigger malicious software on a computer, if that software was already in place when the patch was installed."What to do? Dunno. Wait and see? Sounds good.Wednesday, December 07, 2005
IM Worm 'Chats' to Victims
CNET is reporting a new worm that tricks users on America Online's Instant Messenger to download a .pif file containing a trojan that does the usual evil things. The worm, IM.Myspace04.AIM, appears to respond to keywords. Dubious people asking about possible viruses are assured, "lol no its not its a virus". If this trend continues (oh, it will) make sure you only chat with known users and DO NOT download files unless you have an up to date anti-virus, etc. on your Windows machine. You might also want to try using GAIM IM client.Edited on: Thursday, December 22, 2005 8:36.52 AM EST
| Categories: Alternative Applications, Instant Messaging, Security Alerts, Virus-Trojan-Worm Alerts
Sony Rootkit Patch
SunnComm Makes Security Update Available To Address Recently Discovered Vulnerability On Its MediaMax Version 5 Content Protection Software, Which Is Included On Certain SONY BMG CDs
The full scoop is here: http://www.eff.org/news/archives/2005_12.php#004234. Sony has finally (it appears) got the message that Rootkits are bad. Check the end of the article to determine if you have any of the affected titles and if so download and apply the patch.
| Categories: Best Practices, Privacy Issues, Security Alerts, Software Tools, Virus-Trojan-Worm Alerts

