« Physical Security | Main | RSS Applications »
Saturday, August 06, 2011
Https Everywhere Available
The security add-on for Firefox called HTTPS Everywhere is now available here. This add-on allows for encrypted sessions when you are connected to many of the most popular websites such as Google, Wikipedia, Twitter, Facebook and PayPal. A must have add-on for safely browsing the web.
| Categories: Firefox Extensions, Privacy Issues
Sunday, November 01, 2009
Damn Yer Quiz, Facebook!
I thought Facebook was a means where by one could (virtually) keep in touch with loved ones, friends and colleagues? A place to share pictures and thoughts? Now it appears cluttered with quizzes, games and virus-filled applications. Yeech. Greasemonkey to the rescue!
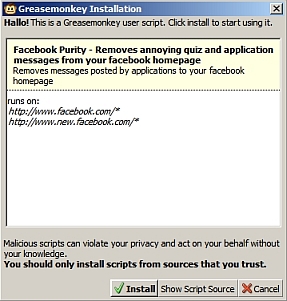
What? Never used Greasemonkey? Hmmm . . . You do use Firefox, right? Check this previous post.
| Categories: Firefox Extensions, Mozilla Firefox, Privacy Issues, Software Tools
Friday, October 09, 2009
Adobe Reader Critical Vulnerability
It appears the ever popular Adobe Reader (version 9.1.3 and earlier) has a gaping hole that could allow bad people to take over Windows installs. This problem as popped up before. One way to mitigate (but not eliminate) the threat is to disable Javascript in Adobe reader and/or change your browsers behavior to download .pdf files as opposed to view them. You also might want to try the free alternative called Foxit Reader which has a better record when it comes to security issues. Just sayin' . . .
| Categories: Alternative Applications, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Tuesday, August 25, 2009
Third-party apps create insecure Facebook
Popular social networking site Facebook has exposed users to phishing attacks that use already hacked accounts to contact friends. Links presented to users lead to look-alike pages not associated with Facebook that may hold any one of 11 rogue scripts (and counting) that do bad things. Trendmicro has details here.
Until facebook tightens up the ship now heading for the shoals be very careful about using third-party apps. Yes, that means a large chunk of facebook, sorry. Do this . . . no, seriously . . . and facebook will adapt or die. Now if Leafs fans would just do the same.
| Categories: Online Apps, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Sunday, May 31, 2009
Pick a Problem
So, if your Windows box is hacked the only person to suffer is you, right? Umm, wrong. Your neglect could allow for many evil happenings to occur. Check out the disturbing graphic of just what may happen here. If you need a full description of the exploits it is here.Friday, February 20, 2009
Adobe Reader Vulnerability
Evil-doers are actively exploiting a security hole in Adobe Reader. Users need only open a rogue .pdf file to have their system taken over.
Since Adobe doesn't plan to patch the problem until March 11th, 2009 users should either disable Javascript within Adobe Reader (Choose "Edit", "Preferences", "Javascript", and uncheck the box beside "Enable Acrobat Javascript") or use an alternative to Adobe Reader called Foxit Reader which is available here: http://www.foxitsoftware.com
| Categories: Alternative Applications, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, February 12, 2009
Facebook Privacy
Check out the handy list of 10 Privacy Settings Every Facebook User Should Know by Nick O'Neill on February 2nd, 2009 at: http://www.allfacebook.com/2009/02/facebook-privacy/| Categories: Best Practices, Online Apps, Privacy Issues
Tuesday, January 06, 2009
Phishing Targets Tweeter
The popular mobile service Tweeter has been hit with phishing messages. Nothing new about this. It is a good time to remind folks about the devious nature of these evil doers. Any method will be used to induce the unwary or stupid to visit sites that will attempt to upload all kinds of malware, spyware, trojans, etc. to your PC, smartphone or other device. The vector for this specific attack is the very popular 'TinyURL' online application that turns large, unwieldy URLs such as “http://www.somewhere.orf/really/long/directory/” into something such as “http://tinyurl.com/4d4a2” which can be remembered long enough to key into a browser. The problem is that the TinyURL could lead one to evil sites. Very bad. TinyURL's solution, which folks either don't know about or don't use or understand is to use the Preview TinyURL. In our previous example one should append the TinyURL with preview: “http://preview.tinyurl.com/4d4a2”. This will allow for the best practice of safely viewing a rendering of the intended target before actually visiting it.| Categories: Best Practices, Headlines, Instant Messaging, Mobile, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Sunday, December 14, 2008
Severe IE Vulnerability
An unpatched vulnerability in Internet Explorer 7 (which also affects older versions of the browser as well) is on the loose. Microsoft has stated that IE 5.01 with SP 4, IE 6 with or without SP 1 and IE 8 (Beta 2) on all versions of the Window OS are affected. To complete the horror IE 7 on Windows XP SP 2 and 3 and Windows Vista with or without SP 1 are also vulnerable. Web sites are now actively exploiting the vulnerability. One has to merely view a Web site in order to have a Trojan horse program automatically downloaded to their machine. Once downloaded the evil doers can manipulate the rogue program to download other software which could perform actions such as sending spam emails or steal data. Since Microsoft's next patch is not due until January 13, 2009 one would be wise to use an alternative browser such as Firefox or Opera. Just sayin' . . .| Categories: Mozilla Firefox, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Wednesday, May 28, 2008
Post-it Passwords
One paragraph in a press report on the recent theft of works by artist Bill Reid astounded me:"(Museum Director Anthony) Shelton said the heist was well organized: three Mexican Zapotec Indian gold-coloured necklaces, which were found despite being hidden in drawers, were the first items taken."Folks . . . you just can't put your passwords on a sticky-note afixed to the underside of your keyboard! Got it?
Edited on: Friday, May 30, 2008 9:25.35 AM EDT
| Categories: Best Practices, Physical Security, Privacy Issues
Patch your Flash NOW
| Categories: Alternative Applications, Mozilla Firefox, Privacy Issues, Security Alerts, Software Tools, Virus-Trojan-Worm Alerts
Thursday, May 15, 2008
US Bound? Secure Your Electronics!
Famed security guru Bruce Schneier has a very imformative article in the UK's Guardian newspaper online. In it he reminds potential visitors to the United States that border agents can and will search through all of your electronic devices. Laptops, cell phones, PDA's, iPods, etc. are all likely targets. Read the whole article here.| Categories: Best Practices, Headlines, Privacy Issues, Software Tools
Wednesday, March 12, 2008
Lessons Learned
It seems G-Archiver, a third-party tool for backing up Google's Gmail, was/is sending usernames and passwords back to evildoers. The lessons here are simple: Always check online to see if the software you are thinking of using is safe. A simple search should confirm if others have any concerns regarding security, privacy, function or usefulness. Secondly, consider trying open-source software when possible. Since these applications are constantly examined by users for problems you tend to be protected in part from hassles that effect proprietary applications.| Categories: Alternative Applications, Best Practices, Privacy Issues, Virus-Trojan-Worm Alerts
Saturday, February 02, 2008
Limewire User Exposes Data
Peer-to-Peer file sharing networks are a haven for Trojans and malware. Letting others into your PC without the proper safeguards (hell, even with the safeguards) is a hole waiting to be filled with evil. If you must use these networks then consider keeping your sharing on your personal machine and not on one used by others.| Categories: Headlines, Privacy Issues
Tuesday, January 22, 2008
How to kill ActiveX
ActiveX is generally a gross security problem waiting to happen within Internet Explorer. Having the ability to kill certain (A few? Some? All but what you really need?) ActiveX controls is detailed by Microsoft here. Or you could use Opera or Firefox in place of Internet Explorer.| Categories: Alternative Applications, Privacy Issues, Security Alerts
Tuesday, November 27, 2007
Unpatched QuickTime Flaw
Those using QuickTime should be aware that a flaw in the most current version could allow attackers to execute code remotely on users machines. While there is no patch available CERT has posted various workarounds to minimize the risk.| Categories: Adware/Spyware Alerts, Privacy Issues, Security Alerts
Saturday, October 20, 2007
RealPlayer Exploit
User of Internet Explorer under Windows are vulnerable to drive-by downloads simply by visiting an evil Web page. As usual, it is an unknown and unpatched ActiveX component that is causing the problem. Note that both Microsoft Outlook and Outlook Express clients are also at risk. Best practices? Uninstall RealPlayer, use an alternative browser such as Firefox or Opera and use another email client such as Thunderbird or Penelope. Those who just can't part with RealPlayer should visit http://service.real.com/realplayer/security/en/ and (when available) download and install the patch. Ryan Naraine over at ZDNet.com has a great write up with info and fixes.| Categories: Adware/Spyware Alerts, Alternative Applications, Best Practices, Mozilla Firefox, Mozilla Thunderbird, Opera, Penelope Email, Privacy Issues, Security Alerts
Sunday, September 30, 2007
AOL AIM IM BUST
Clear as mud, eh? Internet Service Provider AOL has been informed that its IM client has a flaw that makes it possible for evil attackers to remotely execute malicious code on users computers. Those using Internet Explorer are especially vulnerable. Best practices? Try an alternative such as Pidgin (formerly GAIM).| Categories: Alternative Applications, Best Practices, Instant Messaging, Privacy Issues, Virus-Trojan-Worm Alerts
Monday, August 06, 2007
Web 2.0 vs. Privacy Concerns
There is a growing concern that many of the more popular Web 2.0 applications such as Facebook.com or Myspace.com have more than their share of security holes. No doubt. Best practise? Don't give out data anywhere that could compromise your integrity (Nudie photos? Dope smokin' movies? Looking like a doofus?) or security (SIN, birthdate) unless you have faith in the recepient to keep it safe.| Categories: Best Practices, Privacy Issues
Monday, June 11, 2007
OpenOffice.org Virus Spreads
A virus written in numerous scripting languages that can affect Windows, Linux, and Mac OS X computers is slowly spreading via infected OpenOffice.org documents. Best practice is, of course, to never accept documents as attachments in email if you were not expecting them. Inform the sender that it is always best to announce attachments before sending. Having a good Anti-Virus and firewall is also an excellent idea just in case nasties end up on your system. Better safe than sorry!| Categories: Adware/Spyware Alerts, Alternative Applications, Best Practices, Openoffice.org, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Friday, June 08, 2007
Yahoo Messenger Critical Upgrade
Yahoo Messenger has released an upgrade to fix a known security hole that would allow attackers to execute code on your PC. Please upgrade to version 8.1.0.401 from here: http://messenger.yahoo.com/download.php| Categories: Adware/Spyware Alerts, Alternative Applications, Best Practices, Instant Messaging, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Monday, May 14, 2007
Google: 1 in 10 Websites Unsafe
Especially if you use Internet Explorer as opposed to Firefox or Opera. The chance of being nailed by a "drive-by download" is almost non-existent when using any browser other than Internet Explorer. Do yourself a favour and try a safer alternative.
| Categories: Adware/Spyware Alerts, Alternative Applications, Headlines, Mozilla Firefox, Opera, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, March 15, 2007
Phishing vulnerability in IE7
Secunia has a test page where you can determine if your browser is effected. Our tests show Mozilla Firefox 2.0.0.2 and Opera 9.10 to be safe. Internet Explorer 7.0.5730.11 is unsafe. Best practise: Do not use Internet Explorer except to obtain updates for your Windows OS.| Categories: Privacy Issues, Security Alerts
Monday, March 05, 2007
QuickTime Flaw Patched
Apple has patched its QuickTime application for both Mac OS X and all flavours of Windows from 2000 to Vista. Update your version NOW via the software update feature or by going to: http://www.apple.com| Categories: Privacy Issues, Security Alerts
Saturday, January 06, 2007
Adobe Acrobat .pdf Exploit
A serious vulnerabilty in Adobe Acrobat Reader versions prior to version 8 leaves Windows machines open to various attacks. Users, and lets face facts here, that means everyone, should upgrade to version 8.If an upgrade is impossible or unfeasable then, until a patch is issued you should, according to Adobe, disable the Adobe Acrobat Reader plug-in for your Internet browser.
Adobe has the details here: http://www.adobe.com/support/security/advisories/apsa07-01.html
| Categories: Privacy Issues, Security Alerts
Tuesday, October 31, 2006
ZoneAlarm Auto-Update Alarms Users
If you use the ever popular software firewall ZoneAlarm you will have recently seen the first appearance of the new Auto-Update dialogue box indicating that ZA has successfully patched itself. One discussion appears here. Screencaps of the glorious moment are here. If you haven`t spotted the dialogue box it is likely you neglected to download and install the last "full" version which must have included the Auto-Update feature. You are bad, very bad. Update your old ZoneAlarm and bask in the glory of a new Auto-Update tomorrow. (cue triumphant music) Now, why did they not inform its user base of this welcome development before the fact? This is the kind of action that generally prompts me to do a full uninstall as I worry about other processes launching behind my back. Arrgh. I look forward to the full explanation of this behaviour as should you.Edited on: Friday, December 01, 2006 1:13.29 AM EST
| Categories: Best Practices, Headlines, Privacy Issues, Security Alerts
Wednesday, October 18, 2006
Hardware Mayhem
First, it was promotional mp3 players from McDonald's Japan that contained a trojan now it's some Apple Video IPods that shipped with a virus. So, the mantra you must repeat is, "Security is a process NOT a product." Best Practices? Be aware of the possibility of viruses, trojans, etc. appearing in all manner of places and have your defences (Anti-Virus, Firewall, Spyware killers, etc.) ready before you are infected.| Categories: All Things Mac, Best Practices, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Monday, October 02, 2006
USB as CD-ROM
Be aware of the| Categories: Hardware Innovations, Privacy Issues, Security Alerts
Wednesday, August 30, 2006
Persistent data indeed
Remember to always wipe the sensitive data from old devices such as cell phones and PDA's before you part with them. The Globe and Mail has the story here.| Categories: Best Practices, Mobile, Privacy Issues
Tuesday, August 01, 2006
McAfee Flaw
McAfee's whole slew of consumer products is at risk from a flaw that can expose information stored on Windows PC's. Information is here and here. Perhaps it's time to consider an alternative applications such as AVG Free for virus protection?| Categories: Alternative Applications, Headlines, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, July 13, 2006
Adobe Acrobat 'Highly Critical Flaw'
A highly critical flaw has been detected in Adobe Acrobat version 6.0.4 and earlier. If this is you, and it probably is, get thee hence to: http://www.adobe.com/support/downloads to obtain version 6.0.5 or launch Acrobat and use the Auto Update feature.Edited on: Monday, July 31, 2006 4:27.13 PM EDT
| Categories: Best Practices, Privacy Issues, Security Alerts
Saturday, July 08, 2006
Macromedia Flash Player Update
The most recent version is available here:http://www.adobe.com/products/flashplayer/. This fixes a few security boo-boos and is a must have download.Edited on: Monday, July 31, 2006 4:27.03 PM EDT
| Categories: Adware/Spyware Alerts, Privacy Issues, Security Alerts
Tuesday, June 13, 2006
Yahoo! Worm on the Loose
A mass emailer is currently spreading through Yahoo! The worm is activated by simply opening the email message thus making it quite dangerous. The subject line to watch for is: "[random word] New Graphic site".Yahoo is working on the problem. More info here.Edited on: Monday, July 31, 2006 4:26.26 PM EDT
| Categories: Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, June 08, 2006
AutoRun - Tool of the Devil
If you found a USB storage device at your workplace would you plug it into your PC?Edited on: Monday, July 31, 2006 4:26.15 PM EDT
| Categories: Best Practices, Privacy Issues, Security Alerts
Friday, May 19, 2006
W32/Ginwui.A Word Trojan
In these trying times why not try an alternative to Microsoft Word such as Openoffice.org?Edited on: Saturday, May 20, 2006 9:33.12 PM EDT
| Categories: Alternative Applications, Openoffice.org, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Wednesday, May 17, 2006
Poker Players Beware!
If you downloaded RBCalc.exe as distributed by checkraised[dot]com then you have a rootkit on your system! Always check downloads before you make them to ensure they are safe.| Categories: Adware/Spyware Alerts, Best Practices, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Monday, May 15, 2006
Mac Patches You Need
Apple has patched some 31 flaws but according to reports (here and here) there are still flaws that won't be addressed for some time to come :-(| Categories: All Things Mac, Mac Safari Browser, Privacy Issues, Security Alerts
Thursday, May 11, 2006
Firefox mailto: exploit
This exploit could cause your default email client to launch allowing spam to escape. Or it could simply slow down your PC. The quick 'n dirty fix is here.| Categories: Best Practices, Mozilla Firefox, Privacy Issues, Security Alerts
Friday, May 05, 2006
Yahoo Profile Phishing
If you use Yahoo! for IM or email then beware of this phishing web page that spoofs a typical Yahoo! profiles login page hosted on a domain named yahoo-members.com.| Categories: Privacy Issues, Security Alerts
Thursday, April 27, 2006
USB Storage Reality
USB storage devices can host viruses. . . well, duh! If you allow others to use them on your PC take normal precautions.| Categories: Best Practices, Privacy Issues
Friday, April 14, 2006
Kaspersky AV Mobile (BETA)
Kaspersky Labs is offering a BETA version of its Anti-Virus for cell phones using the Symbian OS. Sign up and offer feedback to help improve this application and you may receive a free version of the commercial version.| Categories: Best Practices, Bluetooth, Instant Messaging, Mobile, Privacy Issues, Software Tools
Opera 8.54 Available
Opera 8.54 has been released. This version patches a buffer overflow problem and should be downloaded.| Categories: Best Practices, Opera, Privacy Issues
Sunday, April 09, 2006
Addresses for Reporting Evil
An excellent resource containing email addresses for reporting spam, child porn, OEM software theft, phishing, viruses and more.Thursday, March 30, 2006
Flexispy.A Symbian 60 Trojan / Keylogger
This nasty litle piece of work is actually a commercial product named Flexispy! It records information about voice calls and text messaging sessions. The information is sent to a company server where it can be viewed on the web. Now, I can imagine many scenarios where this type of application could be used in a positive manner but lets get realistic and assume it will be used for nefarious purposes. F-Secure has all the details.| Categories: Adware/Spyware Alerts, Mobile, Privacy Issues, Security Alerts, Software Tools, Virus-Trojan-Worm Alerts
Tuesday, March 28, 2006
Unofficial IE Patches Available
Since Microsoft has announced no patch would (likely) be available for the latest IE vulnerability until April 11, 2006 two patches, here and here, have been authored. Completely unofficially of course but if folks must use Internet Explorer then best practise is to install one of these patches. This is not the first time folks have “stepped into the breach” to cover Bill`s a**.| Categories: Best Practices, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Tuesday, February 21, 2006
Mac Safari Browser Vulnerabilty
Secunia is reporting on a vulnerability in the Safari browser caused by an error in the processing of file association meta data (found in the "__MACOSX" folder) in .ZIP archives. This could cause users to execute a malicious shell script that has been renamed to a safe file extension stored in a .ZIP archive.Worse, it can also be exploited automatically when Safari visits an evil web site.
Secunia has a test available to confirm if your system is vulnerable: http://secunia.com/mac_os_x_command_execution_vulnerability_test/
The vulnerability can be lessened by disabling the "Open safe files after Downloading" option in Safari.
| Categories: All Things Mac, Mac Safari Browser, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Monday, January 16, 2006
Windows WiFi Vulnerability
The Washington Post reports a flaw related to ad-hoc networks on WiFi enabled Windows 2000 or XP machines. The solution, at least until Microsoft patches the flaw, is to use a firewall - this prevents the exploit. The blog has full details: http://blogs.washingtonpost.com/securityfix/2006/01/windows_feature.html.| Categories: Best Practices, Privacy Issues, Security Alerts
Monday, December 19, 2005
Bluetooth Vulnerability
The folks at digitalmunition.com have found a security hole in most Bluetooth software. The skinny is here: http://www.digitalmunition.com/DMA%5B2005-1214a%5D.txt. F-secure has an overview of the problem here: http://www.f-secure.com/weblog/archives/archive-122005.html#00000741.| Categories: Best Practices, Bluetooth, Privacy Issues, Security Alerts
Wednesday, December 07, 2005
Sony Rootkit Patch
SunnComm Makes Security Update Available To Address Recently Discovered Vulnerability On Its MediaMax Version 5 Content Protection Software, Which Is Included On Certain SONY BMG CDs
The full scoop is here: http://www.eff.org/news/archives/2005_12.php#004234. Sony has finally (it appears) got the message that Rootkits are bad. Check the end of the article to determine if you have any of the affected titles and if so download and apply the patch.
| Categories: Best Practices, Privacy Issues, Security Alerts, Software Tools, Virus-Trojan-Worm Alerts
Sunday, November 13, 2005
MS to Remove Sony Rootkit via Anti-Spyware & Malicious Software Removal Tool
Microsoft has decided that the Sony Rootkit poses a threat to its operating systems. Future updates to the Microsoft AntiSpyware application and the now commonly updated Malicious Software Removal Tool will contain the signatures required to remove the truly evil Sony Rootkit. Thanks Bill!| Categories: Adware/Spyware Alerts, Best Practices, Privacy Issues, Software Tools, Virus-Trojan-Worm Alerts
Tuesday, November 08, 2005
Sony Rootkit UNinstaller Almost Worse than Rootkit!
According to Mark Russinovich of Sysinternals.com (the chap who initially discovered the menace) the uninstaller only forces XP to issue the Windows command "net stop" that disables the driver. This inept handling can and has caused XP to crash. The President of Sony BMG's global digital business division Thomas Hesse has explained it all, "Most people, I think, don't even know what a rootkit is, so why should they care about it?" Right. I don't know what Sony stock is either so why should I care if it drops like a rock? Check out the story at The Register here: http://www.theregister.co.uk/2005/11/09/sony_drm_who_cares/ and don't miss the link to the NPR interview with the clueless Sony Prez.| Categories: Adware/Spyware Alerts, Privacy Issues, Security Alerts, Software Tools, Virus-Trojan-Worm Alerts
Thursday, November 03, 2005
Sony Rootkit Uninstaller Available
Sony is now offering users an uninstaller for the Rootkit that would have secretly installed on their PCs if they had placed a Sony music CD in their CD drive anytime after March 2005. While the Rootkit is (probably) not in itself dangerous it does allow hackers a potential entry point into a users PC and for this reason alone should be removed. Bad Sony, bad dog!| Categories: Adware/Spyware Alerts, Privacy Issues, Security Alerts, Software Tools
Tuesday, November 01, 2005
Sony, DRM & Rootkits
Sony BMG is currently using a rootkit-based DRM system on some CD records sold in USA.
The system is implemented in a way that makes it possible for viruses (or any other malicious program) to use the rootkit to hide themselves too. This may lead to a situation where the virus remains undetected even if the user has got updated antivirus software installed.
The quotes above were taken from F-Secure - The whole article is here.
| Categories: Adware/Spyware Alerts, Privacy Issues, Security Alerts
Friday, October 28, 2005
Is your printer spying on you II?
The first entry is herefrom July 25th, 2005. For an updated list of the effected printers go here.Saturday, October 22, 2005
World Of Warcraft = Spyware
It seems the company the produces the popular game World of Warcraft, Blizzard, has been caught reading the processes on users PC's. Now, even though the EULA states this is happening and users could decline it's still a massive invasion of privacy. Read the story here: http://www.eff.org/deeplinks/archives/004076.php and check out the way to "spy on the spy" here: http://www.rootkit.com/newsread_print.php?newsid=371.| Categories: Adware/Spyware Alerts, Privacy Issues, Security Alerts, Software Tools
Tuesday, August 09, 2005
Rogers Yahoo Software Centre
I received an email from my ISP, Rogers.com, letting me know about a new bundle of security applications that are free for subscribers. So far so good. I launch the URL and am taken to the sign-in page and finally to the welcome page, where the whole process screeches to a halt because I am using Firefox and not Internet Explorer. Not supported. You must upgrade to IE 6.

Not bloody likely am I downgrading. I use Firefox and Opera, thanks.
So, I decide to at least fire up my IE 6 (oh, yes, I have it for just these wonderous occasions) and see what Rogers-Yahoo is offering for security.
None of my business it appears! Oh, you get anti-spyware, anti pop-ups, etc but it does not say whose software. I spend my time educatng people to check that what they download is legit and not spyware or virus filled and here my own ISP is keeping its clients in the dark.
Finally, the (limited) info explains that, "As part of the installation process, we will need to check your computer to determine what Rogers Yahoo! software is currently installed."

My goodness, I don't like the sound of that. Do you suppose they may actually be checking to see if the applications on the CD they insist you install upon joining Rogers is still there?
Good intentions badly carried out.
| Categories: Best Practices, Mozilla Firefox, Opera, Privacy Issues
Monday, July 25, 2005
Is your printer spying on you?
The Electronic Frontier Foundation (EFF) reports on their further investigation of a story that first appeared online Nov. 22, 2004 by PC World.". . . several printer companies quietly encode the serial number and the manufacturing code of their color laser printers and color copiers on every document those machines produce. Governments, including the United States, already use the hidden markings to track counterfeiters."
The recent story is here.