« Alternative Applications | Main | Bluetooth »
Friday, February 12, 2010
If you can read this . . .
. . . then your Windows machine hasn't had a BSoD lately I'll guess. It appears one of the updates from Bill has caused mischief
If you have not updated recently you may wish to do a custom update after deselecting KB977165. If you have downloaded the updates but not installed them, again, you may wish to do a custom update after deselecting KB977165. If you have installed it and everything is fine but you are still wary and want it gone then simply go to the Control Panel - Add or Remove Programs (ensure Show updates is checked) - click the Remove button for KB977165.
Best practice is to download but not install for a couple of days. If there is a problem let the rest of the Interpipe sort it out, eh?
Krebs on Security has a (probable) fix here.
Monday, January 18, 2010
Government warnings about IE
When goverments warn about the dangers of using Internet Explorer you can be sure it's time to seek out a alternative application - a safer surfer.
There is, in no particular order, Firefox, Opera and Chrome as well as other browsers.
Do yourself and others a favour by not using Internet Explorer. It's a security hole.
Why, it's like the Adobe Reader of browsers ;)
Go here for links to two of the afore mentioned browsers or you can search for other browser options.
| Categories: Alternative Applications, Best Practices
Wednesday, December 16, 2009
Patching Mania!
Your Windows machine has many, many third-party software applications: Adobe Reader, Apple Quicktime, Google Picasa, Java, Realplayer, Winamp, etc. Heck, even Microsoft has a pile of applications seperate from its OS: Think Media Player, .NET framework, Siverlight, MS Office, etc.
I have in excess of 175 programs!
So, is there an easy way to ensure you 'puter has all the most current (meaning secure) versions of all these applications? Try Secunia Personal Software Inspector.
The first steps include PSI inspecting your entire system for outdated, insecure applications:
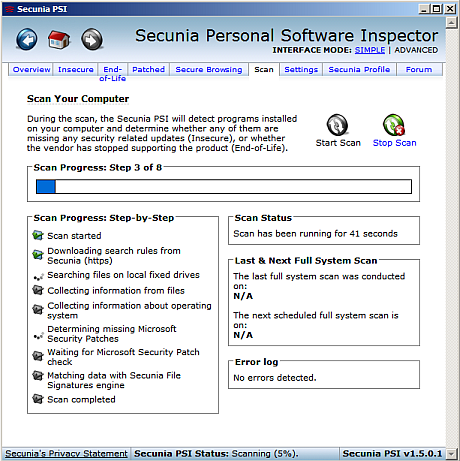
Hopefully the result will look like this:
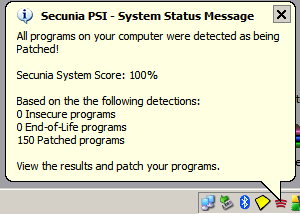
If it does not, well, you have some patching to do. Secunia PSI offers links to the latest versions so manually starting a download is easy. Once patched Secunia PSI stays in the background to monitor your system. If applications upgrade themselves (many do) it will let you know:
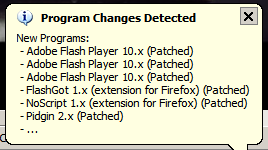
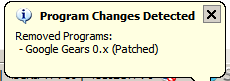
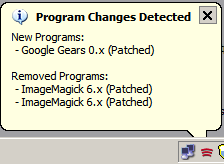
So, I strongly advise those of you who wish to be more secure to download and run this well thought piece of software goodness!
| Categories: Best Practices, Online Apps, Software Tools
Firefox 3.5.6 Available
The latest Firefox has a slew of security and stability fixes and you should upgrade ASAP.
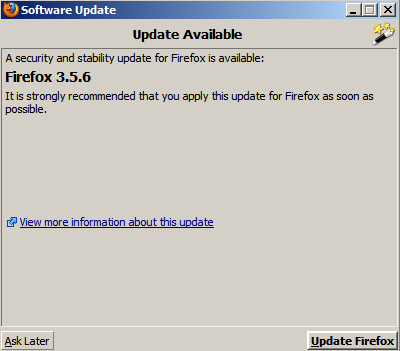
Okey-dokey?
| Categories: Best Practices, Mozilla Firefox
Friday, November 06, 2009
Firefox Update
Y'all better check yer Firefox to see that you are running version 3.5.5 - if you aren't then run a manual upgrade (Help - Check for Upgrades). You might also set Firefox to automagically download and install upgrades:
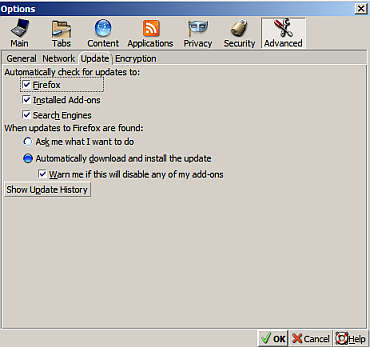
| Categories: Best Practices, Mozilla Firefox, Security Alerts
Sunday, October 18, 2009
Facebook Hacking
A new applications on Facebook, "City Fire Department," has been compromised by hackers. The application had been modified to deliver an iframe which can bring content from one Web site to another. This iframe tries to exploit vulnerabilities to download a fake antivirus program called Antivirus Pro 2010.
A few of the other hacked or bogus applications are:
- MyGirlySpace
- Ferrarifone
- Mashpro
- Mynameis
- Pass-it-on
- Fillinthe
- Aquariumlif
Ok, here is the deal - When you find a wonderful new application on Facebook do a quick search on Google or bing to determine if anyone has had any problem with it. You can also wait, yes wait, for a day or two until enough newbies have started using it to provoke any disasters - if all is well after this then you might . . . might try it. Just make sure your Facebook preferences are locked down for maximum security. Or just don't use any of these silly applications until Facebook gets a grip and uses some mechanism to confirm these applications aren't a giant security hole!
| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Firefox Plugs Microsoft Security Hole
If you use Firefox (and you should, imho) you have probably already seen a pop-up alert informing you that it is blocking Microsoft`s .NET Framework Assistant and Windows Presentation Foundation add-ons that were stealthily installed by Microsoft earlier this year.
This hole was supposed to have been fixed earlier by having users edit the Windows registry - but this idea stunk because editing the registry is potentially dangerous. Microsoft later released a simple point and click removal tool - except this left behind the Windows Presentation Foundation plug-in which is what was just killed by Mozilla.
So, the confusion up to now has been addressed by both Mozilla and Microsoft to remove both nasty bits. Whew!
| Categories: Best Practices, Firefox Extensions, Mozilla Firefox, Security Alerts
Tuesday, April 14, 2009
Twitter Awareness
The recent cross-scripting attack on the newest buzzword universe called Twitter is merely another bump on the rocky road through Interpipe 2.0
These XSS attacks are the bane of Web 2.0 and will cause disasters for individuals who refuse to become aware of their online surroundings. Compound this with users who remain clueless about what is running on their PC's and you have a large impediment in the push through to Web 3.0 applications.
Now add smartphones and netbooks to the mix ;(
For a fine write up on the Twitter XSS attack see: http://twittercism.com/protect-yourself-on-twitter/
Be sure to check out the fine tip from Twittercism about XSS busting using Firefox browser with the Add-on NoScript with screencaps from Better Safe Than Sorry here.
Edited on: Tuesday, April 14, 2009 12:07.58 PM EDT
| Categories: Adware/Spyware Alerts, Best Practices, Firefox Extensions, Mobile, Mozilla Firefox, Online Apps, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, February 12, 2009
Facebook Privacy
Check out the handy list of 10 Privacy Settings Every Facebook User Should Know by Nick O'Neill on February 2nd, 2009 at: http://www.allfacebook.com/2009/02/facebook-privacy/| Categories: Best Practices, Online Apps, Privacy Issues
Patches Make Pefect
On February 10, 2009 Microsoft released four critical patches that could allow evil-doers to take control of an unpatched computer remotely. The updates affect Internet Explorer 7, Windows XP Professional Edition, Windows Vista, Exchange 2000 Server, Exchange Server 2003 and 2007, SQL Server 2000 and 2005 and Office Visio 2002, 2003 and 2007.
The best part of his was the Security Bulletin (MS09-002) that accompanied the patches that stated, "Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights,"
Since probably 90% of folks running any flavour or Windows run as an Administrator most people are at risk here.
If you use Windows try to ensure you do nor run in Adminstrative mode. This is bad. Very bad.
So, ensure your Automatic Updates are turned on and patch early and patch often.
Tuesday, January 06, 2009
Phishing Targets Tweeter
The popular mobile service Tweeter has been hit with phishing messages. Nothing new about this. It is a good time to remind folks about the devious nature of these evil doers. Any method will be used to induce the unwary or stupid to visit sites that will attempt to upload all kinds of malware, spyware, trojans, etc. to your PC, smartphone or other device. The vector for this specific attack is the very popular 'TinyURL' online application that turns large, unwieldy URLs such as “http://www.somewhere.orf/really/long/directory/” into something such as “http://tinyurl.com/4d4a2” which can be remembered long enough to key into a browser. The problem is that the TinyURL could lead one to evil sites. Very bad. TinyURL's solution, which folks either don't know about or don't use or understand is to use the Preview TinyURL. In our previous example one should append the TinyURL with preview: “http://preview.tinyurl.com/4d4a2”. This will allow for the best practice of safely viewing a rendering of the intended target before actually visiting it.| Categories: Best Practices, Headlines, Instant Messaging, Mobile, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Monday, November 10, 2008
WPA Cracked
If you use WiFi to connect to your Internet provider via a wireless router be aware that recently a crack has been found that could allow eavedroppers to detect your passphrase. The simple solution (for now) is to use WPA2 rather than the now vulnerable WPA. If by some chance you missed the memo about the much older WEP protocol you should have stopped using that years ago! If your router does not use WPA2 then ensure it is using AES encryption and not TKIP. Also be damned sure your passphrase is long (12+ characters minimum) and contains a mixture of lower case, upper case, numerals and characters. So, password IS NOT up to scratch. k*uh7%vg4Sk9jNVfdxq)( is just about right ;-)
| Categories: Best Practices, Headlines, Security Alerts
Wednesday, November 05, 2008
Critical Patches Released for Adobe Applications
Adobe has released patches that fix at least eight security holes in both its Acrobat and Adobe Reader programs. These flaws could be used by evil doers to take control of vulnerable systems. Versions 8.1.2 and earlier are affected. Adobe has rated these updates as “critical” indicating that the flaws could allow attackers to comptomise an unpatched system without the users knowledge. The Windows update may be found here.
| Categories: Best Practices, Security Alerts
Monday, November 03, 2008
Opera 9.62 released
The latest version of the safest browser around has been released. You are advised to download and install to patch two security holes that could be used for, among other things, cross-scripting attacks. It is available here: http://www.opera.com/download/| Categories: Alternative Applications, Best Practices, Opera
Friday, October 24, 2008
Critical Microsoft patch available
Microsoft has issued an out-of-band update. This is unusual as Microsoft rarely releases patches ahead of the usual once monthly Patch Tuesday. In this case the severity of the security hole has prompted them to wisely hurry the process along. This update is for XP and Vista although for Vista users it is not deemed critical. What the heck, do it anyway. If you have Windows Update all organized (as you should) you should be safe. If you are unsure if you already have the patch installed then go to Add/Remove Programs in the Control Panel, make sure the check box for show updates is checked:
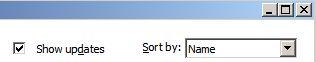
and, when the list is finally displayed look for:
.jpg)
If it's not installed go back to the Control Panel and click on Security Center. Make sure all the settings for Windows Updates, your firewall and whatever anti-virus you use are all functioning as they should.
| Categories: Best Practices, Headlines, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, October 16, 2008
Adobe Flash Upgrade
Adobe has released version 10 of its flash player. This release addresses the so-called Clickjacking attacks where a user could be tricked into clicking a link that would send them to a rogue website. The new version 10 for Windows may be downloaded here.Wednesday, October 15, 2008
Opera Upgraded to 9.60
Time time to visit http://www.opera.com and download the latest and greatest version 9.60 of the most secure browser.| Categories: Alternative Applications, Best Practices, Opera
Saturday, September 27, 2008
Firefox Update Available
Get it while it's hot. This update fixes one bug: ‘’where users were unable to retrieve saved passwords or save new passwords‘’.Yikes.
Click on ‘’Check for Updates‘’ from the Help menu to update and don't forget to restart Firefox for the update to take effect.
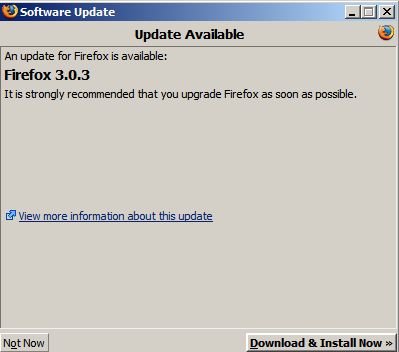
| Categories: Best Practices, Mozilla Firefox
Tuesday, September 23, 2008
Facebook .zip attachment is Bad
People have been getting these fake Facebook 'Add Friends' emails.The evil-doers attached .zip file contains, wait for it you plugs, a Trojan Horse. C'mon, steady, don't fall for that old trick.
Unless you are expecting an attachment don't accept it. Anti-virus blah blah updated frequently blah blah backup daily blah blah idiot, don't be an ;)
| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Wednesday, May 28, 2008
Post-it Passwords
One paragraph in a press report on the recent theft of works by artist Bill Reid astounded me:"(Museum Director Anthony) Shelton said the heist was well organized: three Mexican Zapotec Indian gold-coloured necklaces, which were found despite being hidden in drawers, were the first items taken."Folks . . . you just can't put your passwords on a sticky-note afixed to the underside of your keyboard! Got it?
Edited on: Friday, May 30, 2008 9:25.35 AM EDT
| Categories: Best Practices, Physical Security, Privacy Issues
Tuesday, May 27, 2008
Foxit Reader Security Upgrade
Foxit Reader, a free alternative to Adobe's Acrobat software used for reading .PDF files, has been upgraded. These upgrades recent security holes. Please take the time to download the upgrade from here.| Categories: Alternative Applications, Best Practices
Thursday, May 15, 2008
US Bound? Secure Your Electronics!
Famed security guru Bruce Schneier has a very imformative article in the UK's Guardian newspaper online. In it he reminds potential visitors to the United States that border agents can and will search through all of your electronic devices. Laptops, cell phones, PDA's, iPods, etc. are all likely targets. Read the whole article here.| Categories: Best Practices, Headlines, Privacy Issues, Software Tools
Monday, May 12, 2008
Foxit Reader Upgrade Available
Foxit Reader, a free alternative to Adobe's Acrobat software used for reading .PDF files, has been upgraded. These upgrades plug several security holes. Please take the time to download the upgrade from here.Edited on: Wednesday, May 14, 2008 9:03.05 PM EDT
| Categories: Alternative Applications, Best Practices
Wednesday, March 12, 2008
Lessons Learned
It seems G-Archiver, a third-party tool for backing up Google's Gmail, was/is sending usernames and passwords back to evildoers. The lessons here are simple: Always check online to see if the software you are thinking of using is safe. A simple search should confirm if others have any concerns regarding security, privacy, function or usefulness. Secondly, consider trying open-source software when possible. Since these applications are constantly examined by users for problems you tend to be protected in part from hassles that effect proprietary applications.| Categories: Alternative Applications, Best Practices, Privacy Issues, Virus-Trojan-Worm Alerts
Saturday, October 20, 2007
RealPlayer Exploit
User of Internet Explorer under Windows are vulnerable to drive-by downloads simply by visiting an evil Web page. As usual, it is an unknown and unpatched ActiveX component that is causing the problem. Note that both Microsoft Outlook and Outlook Express clients are also at risk. Best practices? Uninstall RealPlayer, use an alternative browser such as Firefox or Opera and use another email client such as Thunderbird or Penelope. Those who just can't part with RealPlayer should visit http://service.real.com/realplayer/security/en/ and (when available) download and install the patch. Ryan Naraine over at ZDNet.com has a great write up with info and fixes.| Categories: Adware/Spyware Alerts, Alternative Applications, Best Practices, Mozilla Firefox, Mozilla Thunderbird, Opera, Penelope Email, Privacy Issues, Security Alerts
Sunday, September 30, 2007
AOL AIM IM BUST
Clear as mud, eh? Internet Service Provider AOL has been informed that its IM client has a flaw that makes it possible for evil attackers to remotely execute malicious code on users computers. Those using Internet Explorer are especially vulnerable. Best practices? Try an alternative such as Pidgin (formerly GAIM).| Categories: Alternative Applications, Best Practices, Instant Messaging, Privacy Issues, Virus-Trojan-Worm Alerts
Monday, August 06, 2007
Web 2.0 vs. Privacy Concerns
There is a growing concern that many of the more popular Web 2.0 applications such as Facebook.com or Myspace.com have more than their share of security holes. No doubt. Best practise? Don't give out data anywhere that could compromise your integrity (Nudie photos? Dope smokin' movies? Looking like a doofus?) or security (SIN, birthdate) unless you have faith in the recepient to keep it safe.| Categories: Best Practices, Privacy Issues
Wednesday, July 04, 2007
Mpack Intrusion Means Patch Often
Brian Krebs over at the Blog Security Fix has mentioned the availability of the Mpack hackers kit which allows anyone with cash to make serious intrusions into computers and networks. This kit works because folks don't patch all the software on their Windows machines in a timely fashion. If your Windows Operating System is secure but all the software you run is old and unpatched you are vulnerable to this threat. Best Practice? Click on the 'Secunia Software Inspector' icon over in the left column and let Secunia inform you what needs patching. Also sign up for email updates so Secunia can inform you when to re-run the test.| Categories: Best Practices, Security Alerts
Monday, June 11, 2007
OpenOffice.org Virus Spreads
A virus written in numerous scripting languages that can affect Windows, Linux, and Mac OS X computers is slowly spreading via infected OpenOffice.org documents. Best practice is, of course, to never accept documents as attachments in email if you were not expecting them. Inform the sender that it is always best to announce attachments before sending. Having a good Anti-Virus and firewall is also an excellent idea just in case nasties end up on your system. Better safe than sorry!| Categories: Adware/Spyware Alerts, Alternative Applications, Best Practices, Openoffice.org, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Friday, June 08, 2007
Yahoo Messenger Critical Upgrade
Yahoo Messenger has released an upgrade to fix a known security hole that would allow attackers to execute code on your PC. Please upgrade to version 8.1.0.401 from here: http://messenger.yahoo.com/download.php| Categories: Adware/Spyware Alerts, Alternative Applications, Best Practices, Instant Messaging, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Sunday, April 01, 2007
Flaw Allows Critical Windows Exploit
"Upon viewing a Web page, previewing or reading a specially crafted message, or opening a specially crafted e-mail attachment, the attacker could cause the affected system to execute code," sez Microsoft in its advisory. Using any version of Windows, including Vista, and Internet Explorer could lead to catastrophe merely by viewing a web site. Simply viewing an .html page as displayed by most email clients such as Outlook Express could lead the same result. Best Practices? Consider using another browser such as Opera or Mozilla Firefox and/or another email client such as Thunderbird.| Categories: Alternative Applications, Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Saturday, February 24, 2007
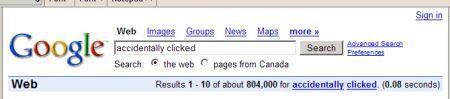
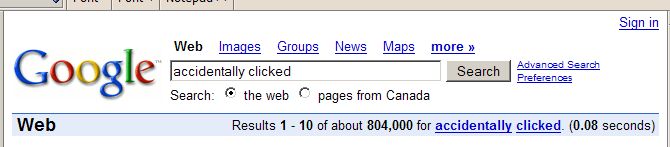
Accidently Clicked Mania!
The screen capture shown below indicates about 804,000 clicks that could have ended in disaster. This is a lot of careless mousing. Take care. Check the links before clicking. Better safe than sorry.Monday, February 19, 2007
Microsoft DST Fix
Beginning on March 11, 2007 daylight saving time (DST) will be extended within most areas of the United States and Canada. DST will start three weeks earlier on March 11, 2007 and end one week later on November 4, 2007. This results in a DST period that will last four weeks longer than was previously observed. Depending on your OS it is possible that the time zone settings may be incorrect during the afore mentioned four week period. Microsoft has a page where you can check to see if you need the fix for this change: http://support.microsoft.com/gp/cp_dst| Categories: Best Practices, Software Tools
Sunday, December 31, 2006
Be Careful of Holiday Greetings Attachments
Since this is the season to sent and receive pictures, songs, and other greetings you must be extra alert to the hidden dangers of email attachments containing evil crap. As always, the best practice is don't click on any link you have doubts about and delete any attachments you were not expecting. Should you in error activate one of these evil things your anti-virus software should stop it. You do have anti-virus software, right?| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Friday, December 08, 2006
MS Word Flaw
Don't accept Microsoft Word .doc attachments via email or Instant Messaging unless you are expecting it and you know the sender. Instead, try Openoffice.org why doncha?| Categories: Alternative Applications, Best Practices
Friday, November 24, 2006
Firefox Password Manager Compromised
It seems a flaw in the way Firefox handles passwords is enabling evil doers to create Phishing holes at sites where .html is allowed such as myspace.com - no fix has been issued but Secunia is advising users to disable the "Remember passwords for sites" option in Firefox preferences.| Categories: Best Practices, Mozilla Firefox, Security Alerts
Tuesday, October 31, 2006
ZoneAlarm Auto-Update Alarms Users
If you use the ever popular software firewall ZoneAlarm you will have recently seen the first appearance of the new Auto-Update dialogue box indicating that ZA has successfully patched itself. One discussion appears here. Screencaps of the glorious moment are here. If you haven`t spotted the dialogue box it is likely you neglected to download and install the last "full" version which must have included the Auto-Update feature. You are bad, very bad. Update your old ZoneAlarm and bask in the glory of a new Auto-Update tomorrow. (cue triumphant music) Now, why did they not inform its user base of this welcome development before the fact? This is the kind of action that generally prompts me to do a full uninstall as I worry about other processes launching behind my back. Arrgh. I look forward to the full explanation of this behaviour as should you.Edited on: Friday, December 01, 2006 1:13.29 AM EST
| Categories: Best Practices, Headlines, Privacy Issues, Security Alerts
Wednesday, October 18, 2006
Internet Explorer 7.0 Released
This version is available here: http://www.microsoft.com/ie/. Best Practise? Download and install for a slight increase in security when your Windows XP just has to use IE.Edited on: Tuesday, October 24, 2006 7:42.49 PM EDT
| Categories: Best Practices, Headlines
Hardware Mayhem
First, it was promotional mp3 players from McDonald's Japan that contained a trojan now it's some Apple Video IPods that shipped with a virus. So, the mantra you must repeat is, "Security is a process NOT a product." Best Practices? Be aware of the possibility of viruses, trojans, etc. appearing in all manner of places and have your defences (Anti-Virus, Firewall, Spyware killers, etc.) ready before you are infected.| Categories: All Things Mac, Best Practices, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Tuesday, September 26, 2006
Windows Vector Markup Language (.VML) Patch
Microsoft has released a patch that fixes the vulnerability found in .VML files. Since this patch has been released outside of the normal update schedule some folks may miss this patch. If this is you then run Microsoft Update NOW.| Categories: Best Practices, Security Alerts
Thursday, September 21, 2006
Windows Vector Markup Language (.VML) Exploit Criticial
Time to unregister a (.dll) file from your Windows XP. If you don't and you use Internet Explorer as your browser you are taking a risk of being owned. This exploit is a drive-by download and you won't even know you're beat. So, Start . . . Run . . . and enter all this:regsvr32 /u "%CommonProgramFiles%\Microsoft Shared\VGX\vgx.dll". . . and hit Return . . . whew, that was close, hmm?| Categories: Best Practices, Security Alerts
Wednesday, August 30, 2006
Persistent data indeed
Remember to always wipe the sensitive data from old devices such as cell phones and PDA's before you part with them. The Globe and Mail has the story here.| Categories: Best Practices, Mobile, Privacy Issues
Thursday, July 13, 2006
Adobe Acrobat 'Highly Critical Flaw'
A highly critical flaw has been detected in Adobe Acrobat version 6.0.4 and earlier. If this is you, and it probably is, get thee hence to: http://www.adobe.com/support/downloads to obtain version 6.0.5 or launch Acrobat and use the Auto Update feature.Edited on: Monday, July 31, 2006 4:27.13 PM EDT
| Categories: Best Practices, Privacy Issues, Security Alerts
Thursday, June 15, 2006
MSN Messenger Worm Spreads
A new worm that seems to be based on an old design (BlackAngel.B / W32/BlackAngel.B.worm) is slowly spreading over the MSN. If you use MSN for chatting only accept files from people and/or sources you trust - even then take all the usual precautions. Best practise is to use a safer IM client such as GAIM for chatting and ONLY chatting - file transfers are best accomplished other ways if you must.| Categories: Alternative Applications, Best Practices, Instant Messaging, Security Alerts
Thursday, June 08, 2006
AutoRun - Tool of the Devil
If you found a USB storage device at your workplace would you plug it into your PC?Edited on: Monday, July 31, 2006 4:26.15 PM EDT
| Categories: Best Practices, Privacy Issues, Security Alerts
Wednesday, May 17, 2006
Poker Players Beware!
If you downloaded RBCalc.exe as distributed by checkraised[dot]com then you have a rootkit on your system! Always check downloads before you make them to ensure they are safe.| Categories: Adware/Spyware Alerts, Best Practices, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, May 11, 2006
Firefox mailto: exploit
This exploit could cause your default email client to launch allowing spam to escape. Or it could simply slow down your PC. The quick 'n dirty fix is here.| Categories: Best Practices, Mozilla Firefox, Privacy Issues, Security Alerts
Thursday, April 27, 2006
USB Storage Reality
USB storage devices can host viruses. . . well, duh! If you allow others to use them on your PC take normal precautions.| Categories: Best Practices, Privacy Issues
Tuesday, April 18, 2006
The Thirty Day Rule
Critical security patches should be applied ASAP. Non-critical patches may wait until any flaws are exposed and fixed. We call it The Thirty Day Rule.Friday, April 14, 2006
Kaspersky AV Mobile (BETA)
Kaspersky Labs is offering a BETA version of its Anti-Virus for cell phones using the Symbian OS. Sign up and offer feedback to help improve this application and you may receive a free version of the commercial version.| Categories: Best Practices, Bluetooth, Instant Messaging, Mobile, Privacy Issues, Software Tools
Opera 8.54 Available
Opera 8.54 has been released. This version patches a buffer overflow problem and should be downloaded.| Categories: Best Practices, Opera, Privacy Issues
Firefox Update Available
The latest version of Firefox that includes several important security updates is available. Click Help . . . Check for Updates.| Categories: Best Practices, Mozilla Firefox, Security Alerts
Tuesday, April 11, 2006
Dude, where are my icons?
After installing todays Microsoft updates confirm your taskbar icons are still visible. If you are a notebook user you may need to see the power meter ;-)Thursday, April 06, 2006
Microsoft Product info via RSS
If you use any flavour of Windows you also, of course, use various and sundry Microsoft applications.Visit this page:
http://support.microsoft.com/selectindex/?target=rss
for a comprehensive list of RSS feeds you can subscribe to that will keep you informed about those products you use.
Thanks Bill!
Wednesday, April 05, 2006
Nuke it Says Microsoft Officer
Your virus ridden, malware choked, adware hounded, trojan infested, rootkit compromised Windows install should be reinstalled suggests a Microsoft Security Officer via The Register. No kidding.Tuesday, March 28, 2006
Unofficial IE Patches Available
Since Microsoft has announced no patch would (likely) be available for the latest IE vulnerability until April 11, 2006 two patches, here and here, have been authored. Completely unofficially of course but if folks must use Internet Explorer then best practise is to install one of these patches. This is not the first time folks have “stepped into the breach” to cover Bill`s a**.| Categories: Best Practices, Privacy Issues, Security Alerts, Virus-Trojan-Worm Alerts
Saturday, February 18, 2006
Later? NO . . . NOW!
According to InfoWorld evildoers have already released Malware that targets flaws in Microsoft products that were patched yesterday. So, those of who have your Windows Update on Automatic are safe but those of you who manually initiate the downloads or who casually thought, "Nah, I'll do it Sunday when I have time" may already be in a world of bad.It is a good idea to set your Windows Update to anything but 'Turn off Automatic Updates'. In fact, if you are the procrastinating type then you should not use 'Notify me but don't automatically download or install them' because by the time you get around to it it may be too late.
If you frequently start up and shut down your PC it may be that even 'Download updates for me, but let me choose when to install them' won't work for you but please try it.
Your best bet is to use 'Automatic (recommended)' so there is no delay in patching your box. If your routine is to boot up your PC every morning at 7:00 AM and start downloading your email whle you brew the coffee why not set your update time to coincide with it? No muss, no fuss. Don't you feel better all ready?
Start - Settings - Control Panel - Security Center: Click Automatic Updates ;-)

Automatic Updates Dialogue Box:
| Categories: Best Practices, Security Alerts
Basic Mac Security
Remember the old adage, security is a process not a product? Well, process this Macheads: A simple list of items you should know/do/avoid when using OS X 10.4 courtesy of user codeport at Mac Geekery.| Categories: All Things Mac, Best Practices
Wednesday, February 15, 2006
Windows Defender Released
Microsoft has released the second beta version of Windows Defender. Formerly called Windows AntiSpyware, the new version can be downloaded here: http://www.microsoft.com/athome/security/spyware/software/default.mspxWe trust this beta version won't pooch anyones Norton Antivirus . . . a recommended download.
| Categories: Best Practices, Software Tools
Saturday, February 11, 2006
MS Anti-Spyware Deleting Symantec's Norton Anti-Virus?
A report in the Washington Post claims that Microsoft support has had complaints that its (Beta) Anti-Spyware application is deleting parts of Symantec's Norton Anti-Virus. Oops. The latest virus definitions seem to believe that Norton is the password stealing Trojan called "PWS.Bancos.A" and so corrupt the Norton install.Remember folks BETA means, "it should work, but don't count on it for mission critical usage".
For now, I suppose run one or the other until they sort this out. Or use AVG instead ;-)
| Categories: Best Practices, Headlines
Monday, January 16, 2006
Windows WiFi Vulnerability
The Washington Post reports a flaw related to ad-hoc networks on WiFi enabled Windows 2000 or XP machines. The solution, at least until Microsoft patches the flaw, is to use a firewall - this prevents the exploit. The blog has full details: http://blogs.washingtonpost.com/securityfix/2006/01/windows_feature.html.| Categories: Best Practices, Privacy Issues, Security Alerts
Thursday, January 12, 2006
Norton SystemWorks Patch
Symantec has patched its Norton SystemWorks following the discovery of a security vulnerability. Users are advised to run LiveUpdate ASAP.| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, January 05, 2006
WMF Exploit Official Microsoft Patch Available
Microsoft has released the official patch designed to close the WMF exploit. If you are running Microsoft Windows 2000 with Service Pack 4 download from here: http://www.microsoft.com/downloads/details.aspx?FamilyId=AA9E27BD-CB9A-4EF1-92A3-00FFE7B2AC74. If you are running Microsoft Windows XP with Service Pack 1 or 2 download from here: http://www.microsoft.com/downloads/details.aspx?FamilyId=0C1B4C96-57AE-499E-B89B-215B7BB4D8E9.| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Sunday, January 01, 2006
WMF Exploit Unofficial Patch
Tests performed on various machines protected by up to date Anti-virus applications have shown that they are almost powerless to stop this series of WMF exploits. On top of the previous best practices an unofficial patch has been released. Understand that Microsoft has no hand in this so if it breaks your OS you are on your own. Since Microsoft appears to not have a fix in the works for a long while this patch is likely a good move until an official fix is released.Remember to first run the command "regsvr32 -u %windir%\system32\shimgvw.dll" (without the quotes) from START - RUN. Assuming you get the OK that the "Microsoft Picture and Fax Viewer" was successfully unregistered then run the patch found here: http://handlers.sans.org/tliston/wmffix_hexblog11.exe.
| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, December 29, 2005
Windows Metafiles (.WMF) Exploits Continue, Part 2
Microsoft has explained how to unregister the Windows Picture and Fax Viewer (Shimgvw.dll):
- Click Start, click Run, type "regsvr32 -u %windir%\system32\shimgvw.dll" (without the quotation marks), and then click OK.
- A dialog box appears to confirm that the un-registration process has succeeded. Click OK to close the dialog box.
NOTE: The Windows Picture and Fax Viewer will no longer open when yous click on a link to an image type that is associated with the Windows Picture and Fax Viewer.
To undo this change, re-register Shimgvw.dll by following the above steps:
- Click Start, click Run, type "regsvr32 %windir%\system32\shimgvw.dll" (without the quotation marks), and then click OK.
- A dialog box appears to confirm that the registration process has succeeded. Click OK to close the dialog box.
| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Wednesday, December 28, 2005
Windows Metafiles (.WMF) Exploits Continue
It appears the real time indexing of metafile data using Google Toolbar is enough to exploit the payload. For now you should disable this indexing of media files until Microsoft issues a patch.You should also add the following sites to your hosts file:
- Crackz.ws
- unionseek.com
- www.tfcco.com
- Iframeurl.biz
- beehappyy.biz
| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Windows Metafiles (.WMF) Exploits
You might add unionseek[DOT]com to your host file. The site is using images, specifically .WMF files (Windows Metafiles), to carry a payload of trojans. Internet Explorer is vunerable, older versions of Firefox and Opera are also at risk but at least they prompt users before they launch external applications ("Windows Picture and Fax Viewer") to view the image. F-secure has the details here: http://www.f-secure.com/weblog/archives/archive-122005.html#00000752. The first I saw of it was at The Register: http://www.theregister.co.uk/2005/12/28/messenger_virus/.| Categories: Alternative Applications, Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Monday, December 19, 2005
Bluetooth Vulnerability
The folks at digitalmunition.com have found a security hole in most Bluetooth software. The skinny is here: http://www.digitalmunition.com/DMA%5B2005-1214a%5D.txt. F-secure has an overview of the problem here: http://www.f-secure.com/weblog/archives/archive-122005.html#00000741.| Categories: Best Practices, Bluetooth, Privacy Issues, Security Alerts
Wednesday, December 14, 2005
Fake McAfee Site via Email Links
F-Secure has reported instances of fake emails from McAfee with links that point to a bogus site with downloads that contain viruses. Applications do not update themselves by having their parent company send emails encouraging users to visit sites. Be aware what software is installed on your PC. Determine which of these update automagically and keep a grip on what URL's correspond to what websites. If in doubt do not click that link! Never respond to unsolicited emails.| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
The Thirty Day Rule
An old Javascriprt vulnerability in all Firefox versions prior to 1.0.5 has taken on a new life since the code to take advantage of it has been published on the web. Those of you who are still happily using older versions should upgrade. Best Practices: Always upgrade to the latest version of software at about the thirty daymark after its release because . . . a) This gives any bugs in the release time to be found by all those early adopters allowing the developers time to patch the bug. b) Not enough time has passed that evil virus writers have released exploits. c) Authors of plugins and other add-ons (such as Firefox extensions) will have had time to patch their products.| Categories: Best Practices, Mozilla Firefox, Security Alerts
Wednesday, December 07, 2005
Sony Rootkit Patch
SunnComm Makes Security Update Available To Address Recently Discovered Vulnerability On Its MediaMax Version 5 Content Protection Software, Which Is Included On Certain SONY BMG CDs
The full scoop is here: http://www.eff.org/news/archives/2005_12.php#004234. Sony has finally (it appears) got the message that Rootkits are bad. Check the end of the article to determine if you have any of the affected titles and if so download and apply the patch.
| Categories: Best Practices, Privacy Issues, Security Alerts, Software Tools, Virus-Trojan-Worm Alerts
Sunday, December 04, 2005
Object Lesson in Keeping Current
Much like no one likely suspected that Sony would be involved in Rootkits we have a story about hardware containing a trojan. F-secure has the scoop and the previous horrors: http://www.f-secure.com/weblog/archives/archive-112005.html#00000723. The companies had no intention of placing these trojans but you must always be aware of your own security. Be aware that hardware and/or software could be compromised. So, always have an updated anti-virus running and run applications designed to catch spyware, adware and other evils.| Categories: Best Practices, Security Alerts
Tuesday, November 22, 2005
Beware the Sober.Y virus
Beware of emails purporting to come from official security agencies such as the FBI, CIA or German BKA. Like the previous ones this virus sends itself inside a ZIP archive as an attachment in email messages with English or German texts. All the details are here: http://www.f-secure.com/v-descs/sober_y.shtml.
Never open unexpected attachments. Always have an updated anti-virus installed.
Edited on: Thursday, November 24, 2005 8:27.51 AM EST
| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Sunday, November 13, 2005
MS to Remove Sony Rootkit via Anti-Spyware & Malicious Software Removal Tool
Microsoft has decided that the Sony Rootkit poses a threat to its operating systems. Future updates to the Microsoft AntiSpyware application and the now commonly updated Malicious Software Removal Tool will contain the signatures required to remove the truly evil Sony Rootkit. Thanks Bill!| Categories: Adware/Spyware Alerts, Best Practices, Privacy Issues, Software Tools, Virus-Trojan-Worm Alerts
Friday, November 11, 2005
Time to Update ReaPlayer
Secunia is reporting the 'ole buffer overflow in RealPlayer, RealOne and HelixPlayer. Time to upgrade! That includes you Mac Heads, right?Edited on: Wednesday, November 30, 2005 9:24.41 PM EST
| Categories: All Things Mac, Best Practices, Security Alerts
Thursday, November 10, 2005
Trojans Using Sony Rootkit
Those dumbasses at Sony can thank themselves now that the first and second Trojans have been found in the wild - both Trojans use the oft mentioned Rootkit to hide themselves - the exact thing that Sony claimed would not happen. The details from F-Secure are here: http://www.f-secure.com/v-descs/breplibot_c.shtml. This is a good time to remind you to make sure you have the usual precautions in place: updated anti-virus, organized firewall(s) and some common sense.| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Thursday, November 03, 2005
Mac OS X 10.4.3 Update (Delta)
Apple has introduced a minor fix for OS X - Read about it here: http://docs.info.apple.com/article.html?artnum=301984.| Categories: All Things Mac, Best Practices, Security Alerts
Friday, September 09, 2005
Firefox Patched !
Several minutes after the security hole was discovered a few workarounds were finished - Go here: https://addons.mozilla.org/messages/307259.html. The easiest method is to install the extension.| Categories: Best Practices, Security Alerts
Tuesday, August 30, 2005
Internet Explorer Exposes Clipboard Data
Microsoft's Internet Explorer exposes clipboard data via javascript with no security confirmation. Ever work on your company payroll or other sensitive material in Excel? Did you "copy and paste" any of the data? Anywhere you surfed after that could possibly be collecting that data. There is no fix for this and while it is highly unlikely you will pass data on to evil people you should clear your clipboard before surfing the web. Or use Firefox or Opera instead of Internet Explorer.| Categories: Alternative Applications, Best Practices, Security Alerts
Friday, August 19, 2005
Msdds.dll + Active-x = Bad
A file that does not normally ship with Windows but that is included with downloaded applications such as the .NET framework has the potential to to be used maliciously. Details on the file, Msdds.dll, can be found at Secunia and Microsoft. Run a search on your Windows PC and determine if you have the file - if not, you're safe. If you do have it then keep your eyes open for a patch from Microsoft in the near future. Until then keep an even closer eye on mysterious sites asking you to OK the running of Active-x scripts. Remember, the added functionality of Active-x is compromised by its lack of security so limit your Active-x controls to known safe sites if possible.| Categories: Best Practices, Security Alerts
Monday, August 15, 2005
Zotob.A & Zotob.B Target W2K
Those of you still running Windows 2000 have to be aware of two nasty new Trojans named Zotob.A and Zotob.B - The worm attempts to connect to an IRC channel at a predefined address allowing attackers to, among other things, request system information and download/execute files. Access to numerous security related sites via the hosts file is also disabled.Patches for this vulnerability have only been available for five days. Keeping abreast of critical security flaws and patching them quickly is your best defence. Never put off a security re-boot until tomorrow - it may be too late.
| Categories: Best Practices, Security Alerts, Virus-Trojan-Worm Alerts
Tuesday, August 09, 2005
Rogers Yahoo Software Centre
I received an email from my ISP, Rogers.com, letting me know about a new bundle of security applications that are free for subscribers. So far so good. I launch the URL and am taken to the sign-in page and finally to the welcome page, where the whole process screeches to a halt because I am using Firefox and not Internet Explorer. Not supported. You must upgrade to IE 6.

Not bloody likely am I downgrading. I use Firefox and Opera, thanks.
So, I decide to at least fire up my IE 6 (oh, yes, I have it for just these wonderous occasions) and see what Rogers-Yahoo is offering for security.
None of my business it appears! Oh, you get anti-spyware, anti pop-ups, etc but it does not say whose software. I spend my time educatng people to check that what they download is legit and not spyware or virus filled and here my own ISP is keeping its clients in the dark.
Finally, the (limited) info explains that, "As part of the installation process, we will need to check your computer to determine what Rogers Yahoo! software is currently installed."

My goodness, I don't like the sound of that. Do you suppose they may actually be checking to see if the applications on the CD they insist you install upon joining Rogers is still there?
Good intentions badly carried out.
| Categories: Best Practices, Mozilla Firefox, Opera, Privacy Issues
New Symbian Trojan
What would you do if the new application you just copied to your Symbian cell phone caused the fonts to disappear? Well, if you insist on visiting dodgy sites to download pirated software you may son have real world experience on the issue. A new trojan named SymbOS/Blankfont.A is waiting for you at a Warez site now!Todays lessons learned:
- Never install an application on any device unless you have searched the Internet and came up blank on horror stories.
- Do not use pirated software.
- Stay away from sites that have evil intent or conduct illegal activities.
| Categories: Best Practices, Mobile, Virus-Trojan-Worm Alerts
Saturday, August 06, 2005
CoolWebSearch Spyware Uncovered
Identity theft via CoolWebSearch has apparently been uncovered. If true, and the facts are not yet comfirmed to my satisfaction, this massive illegal harvesting of financial and personal information may hopefully wake folks up regarding the potential security risks when using an unprotected Windows OS. Use a firewall and anti-virus software. Buy a hardware router. Install and run anti-spyware applications. Do not run your Windows in Administrator mode. Get a grip, dammit!| Categories: Adware/Spyware Alerts, Best Practices
Saturday, July 30, 2005
Standing Behind Accordion Guy
Moving in Toronto? Need to hire a competent moving company? Do not use Quick Boys.Well, according to Accordion Guy they are don't do a very good job. Worse, they threatened him. So let's shine a big light on these folks to let them know this kind of crap is unacceptable in OUR Toronto.
| Categories: Best Practices, Security Alerts
Tuesday, July 26, 2005
Day One of Windows Genuine Advantage Programme
That's right boys and girls Bill is no longer going to update your "non-genuine versions" of Windows XP.They will continue to update pirated versions as long they are authenticated. This will ensure that those copies out there will not be copied.
Users need to visit the Microsoft Download Centre, Windows Update or Microsoft Update where they will be required to download an ActiveX control. This will check the authenticity of their Windows install and, if validated, allow for future verification.
Visit the Windows Genuine Advantage Programme.
| Categories: Best Practices, Headlines
Tuesday, July 19, 2005
Mandatory Greasemonkey Update
Users of Greasemonkey are strongly urged to either install Greasemonkey 0.3.5, or else disable or uninstall Greasemonkey completely. A security flaw allows any website which matches at least one user script (even * scripts) to read any local file on your machine, or to list the contents of local directories.
Edited on: Wednesday, July 20, 2005 6:30.38 PM EDT
| Categories: Best Practices, Mozilla Firefox
Tuesday, June 28, 2005
Longhorn RSS Support
While browsing the web, users will be able to easily discover RSS feeds through an illuminated icon, as well as read the feed while still in the web browser. Additionally, users will be able to subscribe to an RSS feed as easily as adding a web page as a favorite. Once a user chooses to subscribe to a feed, the fact that the user has subscribed is available to any interested application.
Uh-huh. How long will it take until some nasty script automatically and in the background subscribes me to ad-driven crap that proceedes to infiltrate to my other interested applications?
Unless the security of Internet Explorer + Longhorn is substantially improved there is no way in hell I'm letting this loose on my system.
Edited on: Wednesday, July 20, 2005 4:14.47 PM EDT
| Categories: Best Practices, RSS Applications
Tuesday, April 19, 2005
Norton Internet Security 2005 AntiSpyware
Symantec today released their Anti-Spyware application - Norton Internet Security 2005 AntiSpyware Edition. I downloaded it and was in the middle of the install when the following dialogue box appeared:
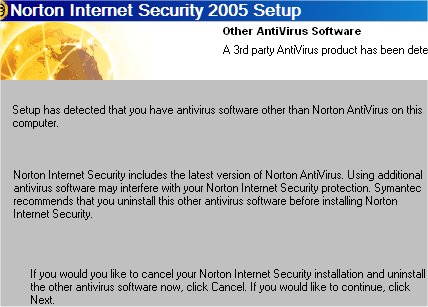
>Well, thanks but no - what makes them think I
want their damn anti-virus? Perhaps if I had no
protection this would be a treat but to have them suggest I uninstall my
present Anti-virus seems a tad arrogant to me. Sorry Symantec, you're
tactic is not appreciated and therefore I will not
be installing your application until it is a stand-alone anti-spyware
client.
Edited on: Monday, July 25, 2005 1:23.56 PM EDT
| Categories: Best Practices, Security Alerts
Opera 8 Released
It has increased security, pop-up blockers, an RSS aggregator, is fully tweakable and has the ultra-cool voice commands!
You haven't lived until you have barked, " Opera, next link!" at your computer.
Edited on: Wednesday, July 20, 2005 4:38.43 PM EDT
| Categories: Alternative Applications, Best Practices, Opera
Monday, April 18, 2005
Firefox Extension: Formfox
The extension is called Formfox - it's purpose is to alert you to where the information in an online form is being sent to.
This is an excellent way to prevent folks from being taken in by a fake site that asks for legitimate information that is forwarded to evildoers.
When your mouse is hovering over the button that submits a form an URL will display showing where your information is actually going. If, for example, you believe you are at the your online bank and the URL displayed by Formfox is [http://russian-mafia.ru] you may well not press that button!
| Categories: Best Practices, Mozilla Firefox
Wednesday, April 06, 2005
CRTC: VoIP firms must carry 911 services
Watching rogers.com provide this service should be fun if the past performance is any indication:
"Press 1 if you are on fire, Press 2 if you are being assaulted, Press 3 if you need to speak to . . . click . . . "
Edited on: Wednesday, July 20, 2005 5:26.15 PM EDT
| Categories: Best Practices
Monday, March 14, 2005
Java Applet trojan
>
>So, if you have Java switched on in your browser and a dodgy website asks you whether you want to run Java applet, just answer no.
>
>To be absolutely safe turn off Java. Ooh, but you'll miss all the bounching balls and goofy sound effects. End sarcastic comment.
Edited on: Wednesday, July 20, 2005 5:36.32 PM EDT
| Categories: Adware/Spyware Alerts, Best Practices
Saturday, March 05, 2005
Baggage Checklist
Edited on: Wednesday, July 20, 2005 5:37.11 PM EDT
| Categories: Best Practices
Thursday, February 10, 2005
Future Threats
Ack.
Edited on: Wednesday, July 20, 2005 5:43.49 PM EDT
| Categories: Adware/Spyware Alerts, Best Practices, Bluetooth, Mobile, Security Alerts, Technology, Virus-Trojan-Worm Alerts
Monday, January 17, 2005
No More Internet for Them
The article has no mention of alternatives to Windows OS, browser alternatives to Internet Explorer or email alternatives to Outlook Express.
Sigh.
Edited on: Wednesday, July 20, 2005 5:59.43 PM EDT
| Categories: Adware/Spyware Alerts, Alternative Applications, Best Practices, Concepts, Eudora Email, Mozilla Firefox, Mozilla Thunderbird, Openoffice.org, Opera, Software Tools
Tuesday, January 11, 2005
Hackers Tune In to Windows Media Player
Edited on: Wednesday, July 20, 2005 6:01.22 PM EDT
| Categories: Alternative Applications, Best Practices, Software Tools, Virus-Trojan-Worm Alerts
Thursday, January 06, 2005
Microsoft Releases Anti-Spyware beta
Security has always been a weak point at Microsoft and this problem has, up until recently, been solved by third-party software vendors who have produced well thought out applications to save us from evildoers.
Since Bill has seen the light we have received Microsoft Firewall and now the Microsoft Anti-Spyware beta.
I would suggest you at least try the Anti-Spyware and see if it offers any increased security when used in conjunction with established Anti-Spyware applications - remember this is BETA and may not work quite as expected.
Several lunatics at slashdot.org claim the validation procedure can be ignored. Your mileage may vary.
Comments welcome from all those with busted Windows OS's and you Windows 2000 beta users - you know who you are . . .
Edited on: Wednesday, July 20, 2005 6:03.21 PM EDT
| Categories: Adware/Spyware Alerts, Best Practices
E-mail used as weapon in court case
If, however, that dog sends email there is every chance that somewhere that email exists - on a personal computer, as a USENET archive or on some hard drive in a long lost Hotmail account.
So . . . always assume that any email you send will be read by your Mother and then posted on the telephone pole outside your house.
Edited on: Wednesday, July 20, 2005 6:03.34 PM EDT
| Categories: Best Practices
Thursday, December 30, 2004
New Cabir Variants are Spreading Fast
Edited on: Wednesday, July 20, 2005 6:13.03 PM EDT
| Categories: Best Practices, Bluetooth, Mobile, Virus-Trojan-Worm Alerts